Around two years ago, I wrote an article for "Managing iOS Devices with Microsoft Intune," a lot has happened since then. The transition from legacy authentication to modern authentication by both Apple and Microsoft has completely changed the way devices are enrolled to MDM in both COD and

Around two years ago, I wrote an article for "Managing iOS Devices with Microsoft Intune," a lot has happened since then. The transition from legacy authentication to modern authentication by both Apple and Microsoft has completely changed the way devices are enrolled to MDM in both COD and BYOD scenarios. So, here is an AIO guide to help you plan, prepare, manage, and secure your Apple platform using Microsoft Intune.
What we will cover in this series:
Before you begin enrolling Apple devices in Intune, it is essential to review & understand the requirements or use cases so that you can define the approach:
The below table should give you a fair idea about the different approaches:
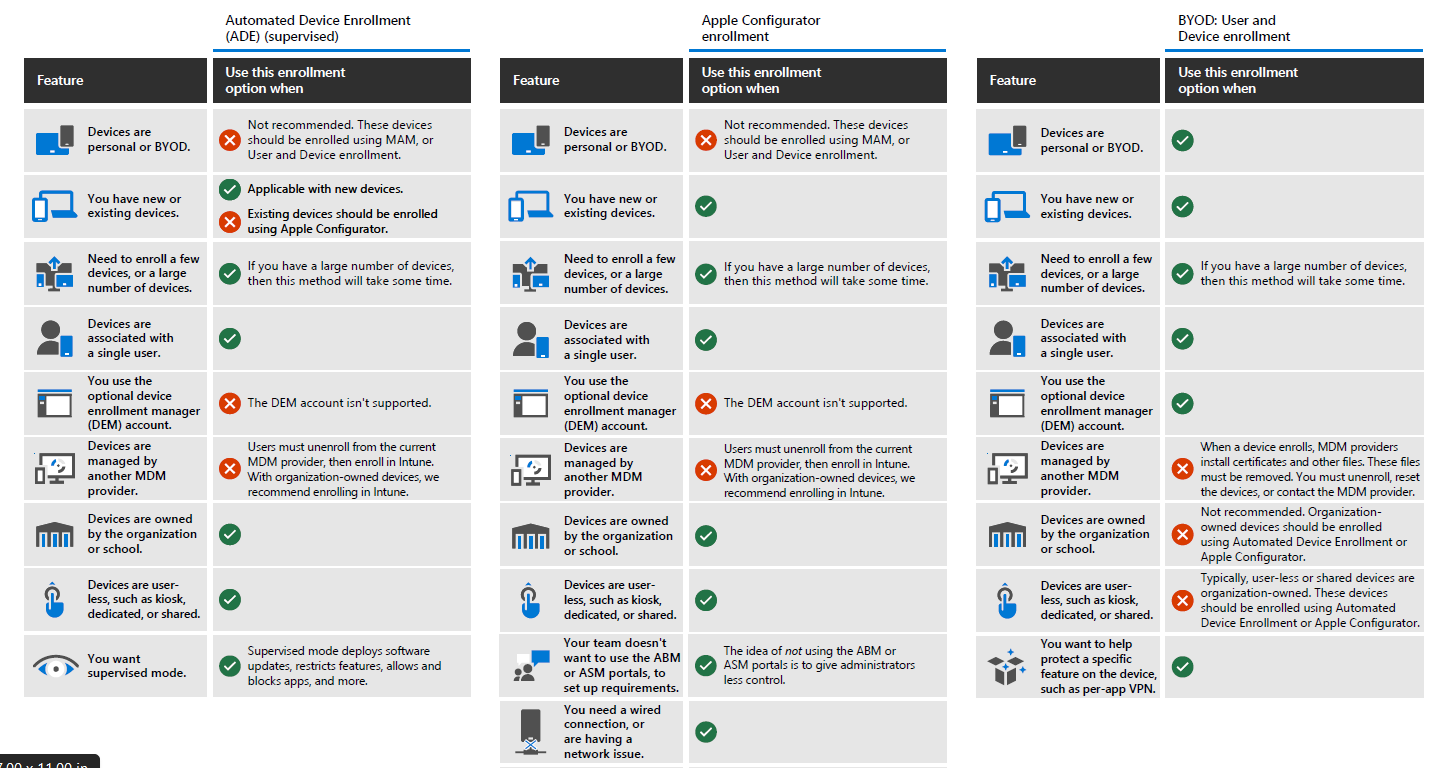
For all Intune-specific prerequisites and configurations needed to prepare your tenant for enrollment, see the Enrollment guide: Microsoft Intune enrollment.
In today's world, for any organization, its most valuable asset is "data". Whether accessed from the end user's own devices or the devices given by the organization, keeping corporate data safe is one of the most challenging yet critical measures. When talking about Apple devices, Apple has made it simple for IT to accommodate various device management checks without impacting end users' productivity or privacy.
Apple gives IT teams the tools to be successful and have the control they need without compromising usability. This is achieved through the tight integration of Apple’s management framework and your mobile device management (MDM) solution.
In iOS, iPadOS, tvOS, and macOS, Apple includes a management framework that allows IT to configure and update settings, deploy apps, monitor compliance, query devices, and remotely wipe or lock devices. This framework supports corporate-owned and personally-owned devices and is the foundation for deployment and management. MDM solutions are available from a wide range of vendors who offer a choice of features and prices for maximum flexibility, regardless of whether an enterprise deploys a cloud-based or an on-premise server.
No matter what deployment strategy you choose, the MDM framework will never have access to your email, messages, or browsing history.
Management of these devices can take many forms, depending on company needs and security concerns. The main device ownership models cover a wide spectrum of business requirements:
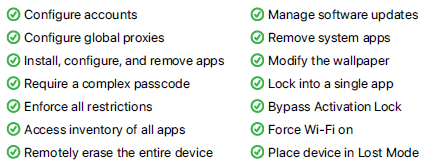
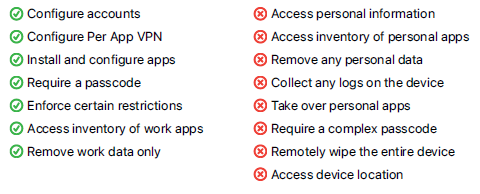
Any organization's security strategy must include device management as a critical element. To prevent unwanted access to the corporate network and data, it ensures that devices are safe, updated, and comply with organizational regulations. A sound device management strategy is more crucial than ever as businesses accommodate remote and hybrid workforces. Organizations are required to safeguard and secure all of their data and resources.
Microsoft Intune helps you to secure proprietary data that users access from their company-owned and personally-owned devices. Intune includes device and app policies, software update policies, and installation statuses (charts, tables, and reports).
In general, there are two methods for managing devices.
While you design your device management infrastructure, don't forget to consider these two critical points:
I'll end this section right here, so let's get started on part 2 of the series.