Imagine a scenario: Your Mac fleet houses a growing universe of data, valuable and vulnerable in equal measure. This ever-expanding data sprawl threatens to spiral out of control, a potential security nightmare. But fear not, for there's a guardian in the wings: mSCP. This isn't a

Imagine a scenario: Your Mac fleet houses a growing universe of data, valuable and vulnerable in equal measure. This ever-expanding data sprawl threatens to spiral out of control, a potential security nightmare. But fear not, for there's a guardian in the wings: mSCP.
This isn't a secret government agency (though it sounds like it could be), but a powerful tool that can revolutionize your Mac data security. Developed through a collaborative effort between the National Institute of Standards and Technology (NIST), National Aeronautics and Space Administration (NASA), Defense Information Systems Agency (DISA), and Los Alamos National Lab (LANL), mSCP equips you with a programmatic approach to generating security guidance, empowering you to Secure, Contain, and Protect your Mac data like never before.
This blog post will be your guide to wielding mSCP like a seasoned pro. We'll delve into the "why" and "how" of using mSCP, transforming you from a data security novice into a master of your Mac domain. So, buckle up and get ready to learn how mSCP can be your secret weapon in the fight for watertight Mac data security!
The ever-evolving landscape of Mac data presents a unique challenge for IT professionals. Here's why mSCP emerges as a vital tool:
Now that we've established the urgency of managing your Mac data menagerie, let's dive into the specific benefits mSCP offers:
Now that you're armed with the knowledge of mSCP's benefits, let's roll up your sleeves and get started! Here's a roadmap to guide you through the mSCP implementation process:
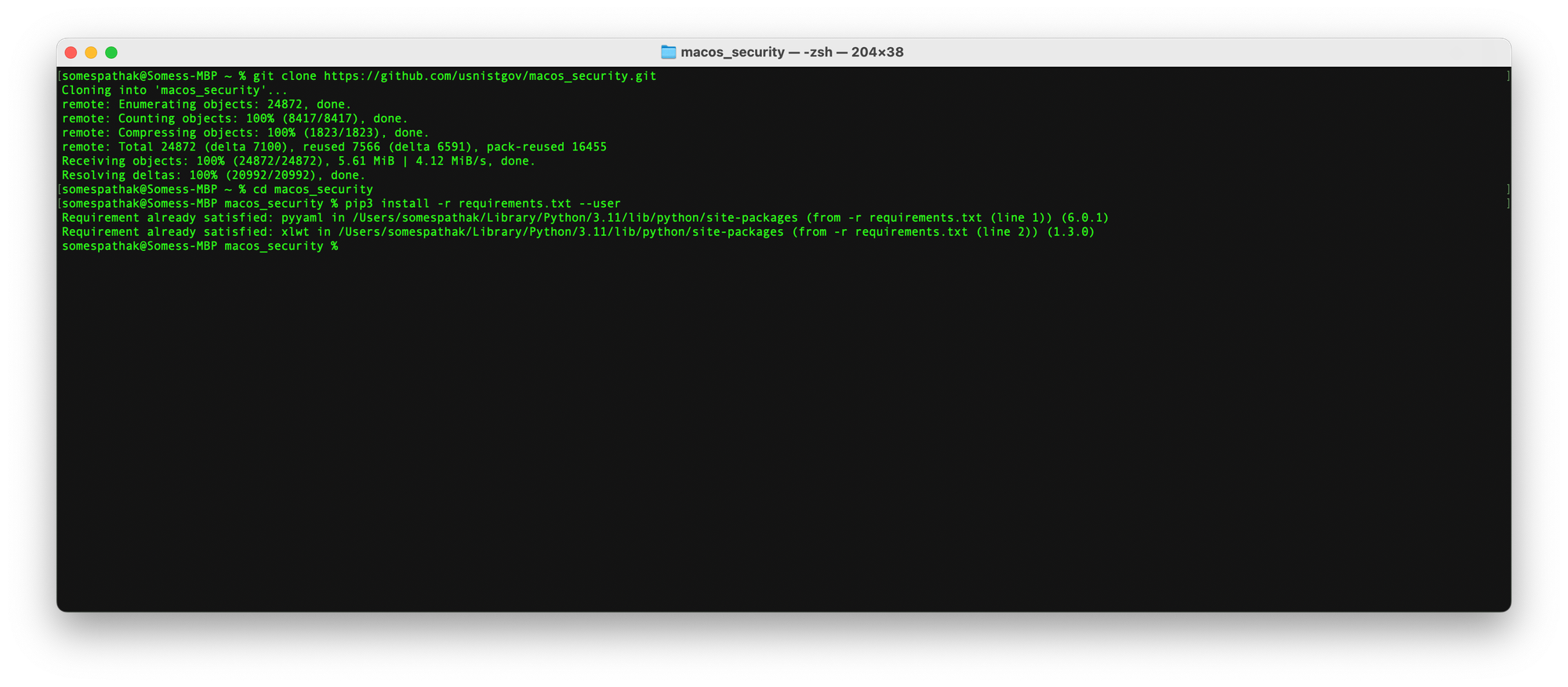
mkdir macOS_securitycd macos_security git clone https://github.com/usnistgov/macos_security.git
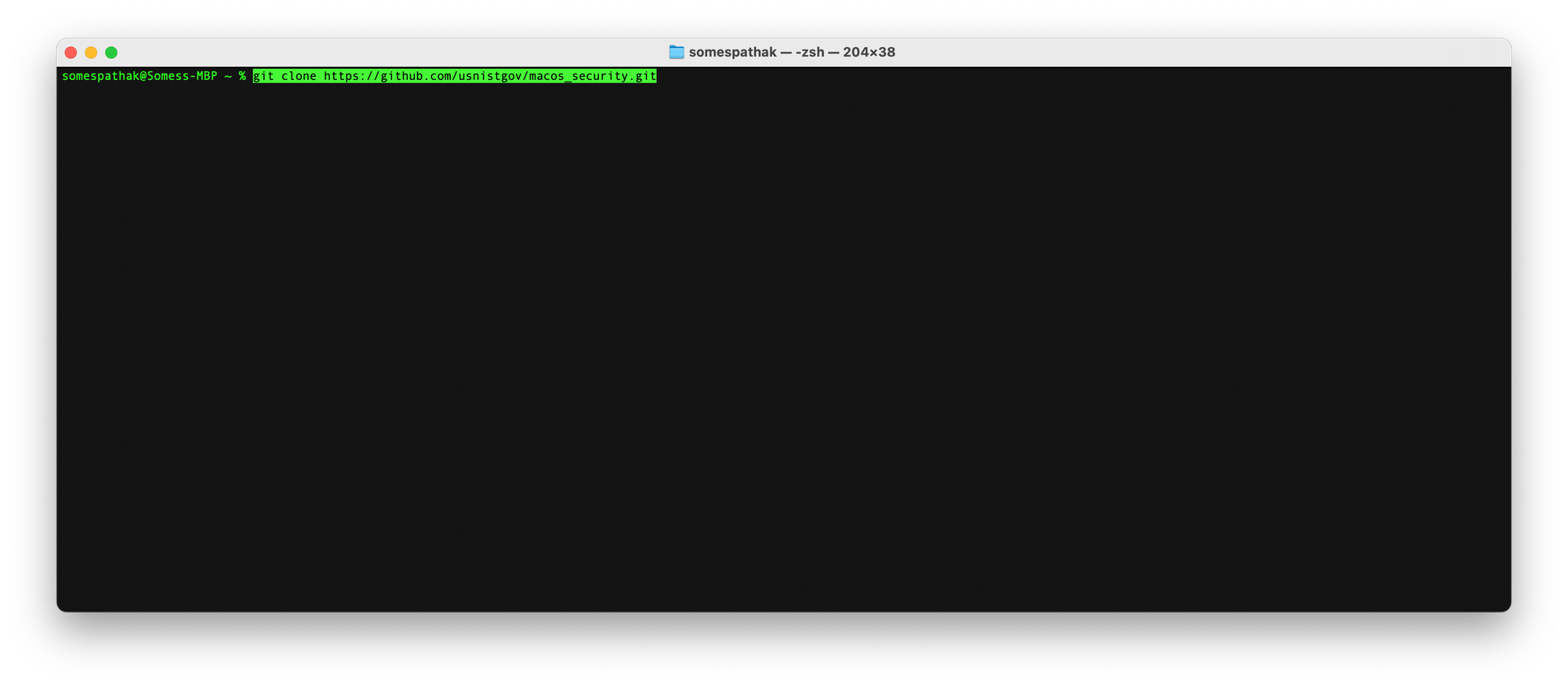
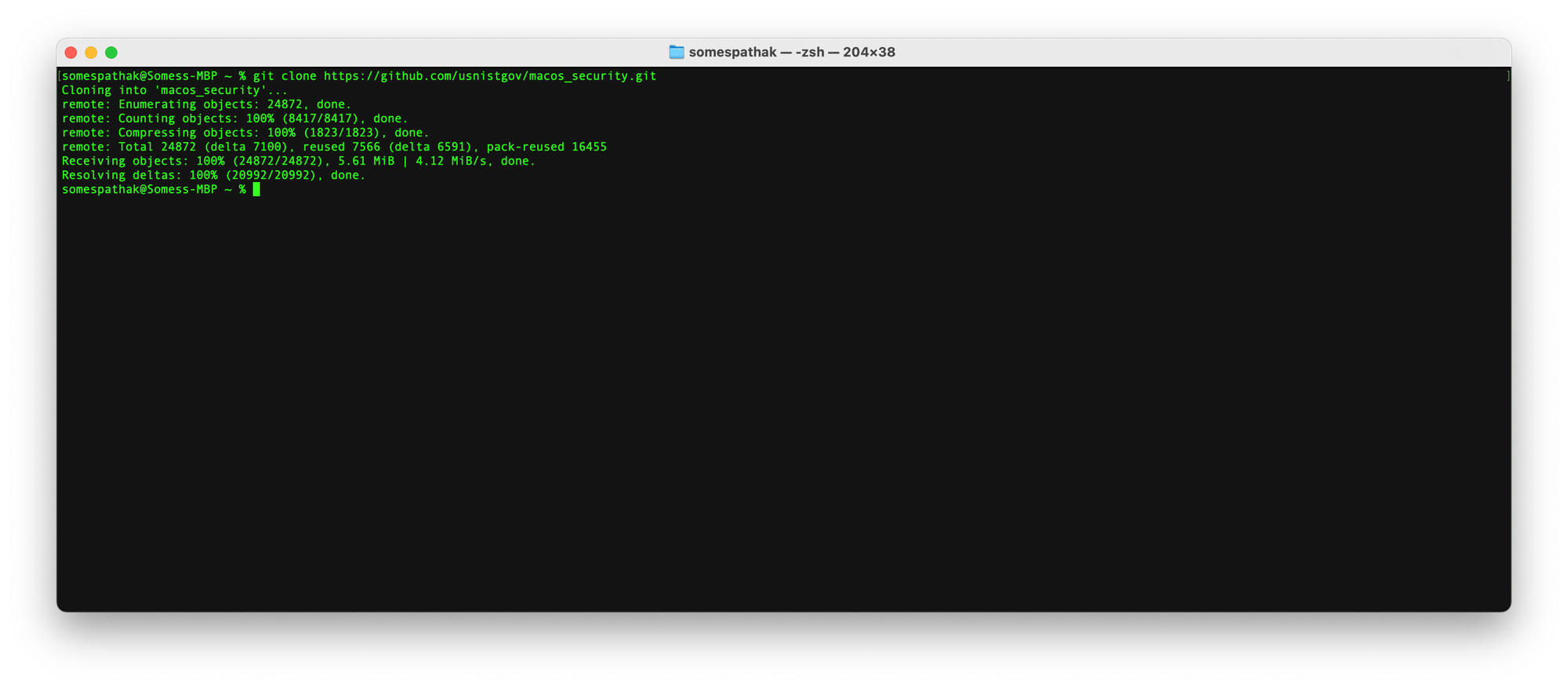
cd macos_security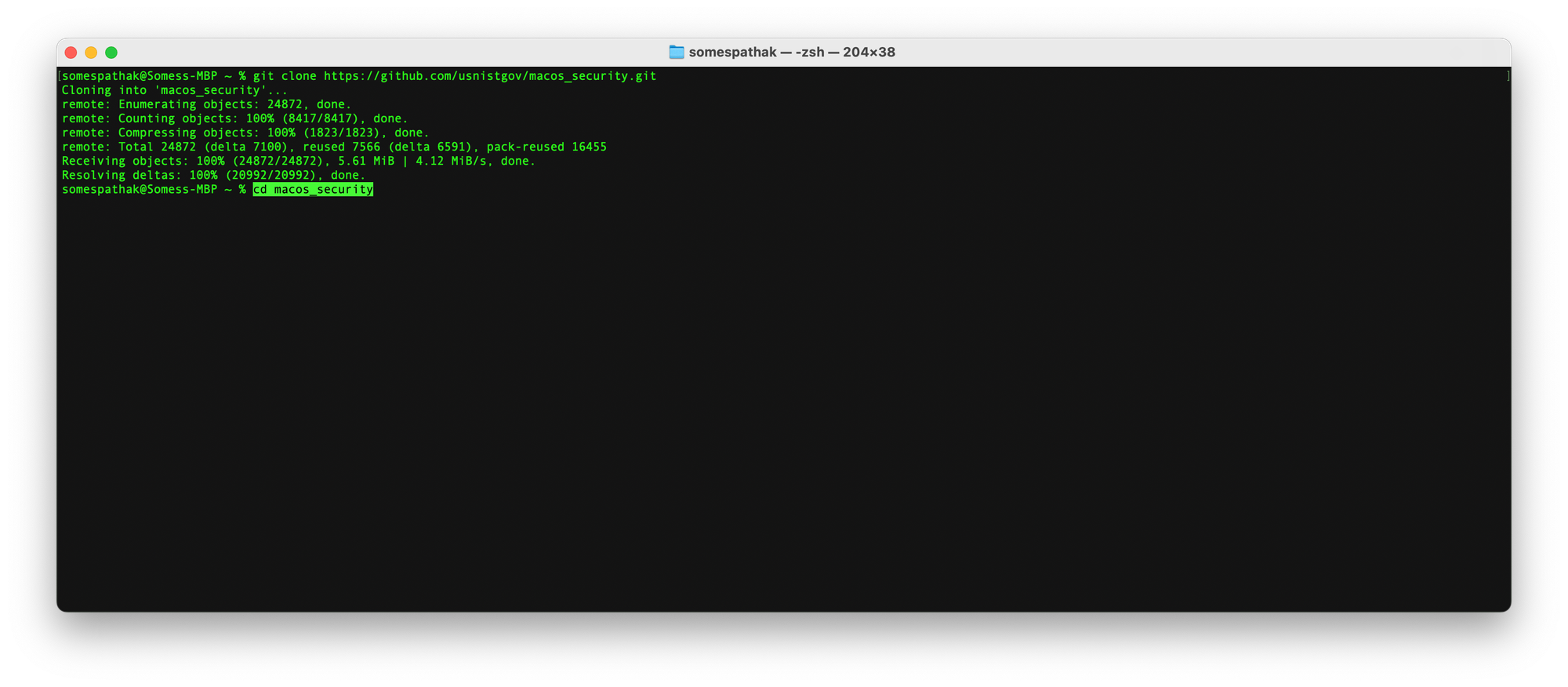
pip3 install -r requirements.txt --user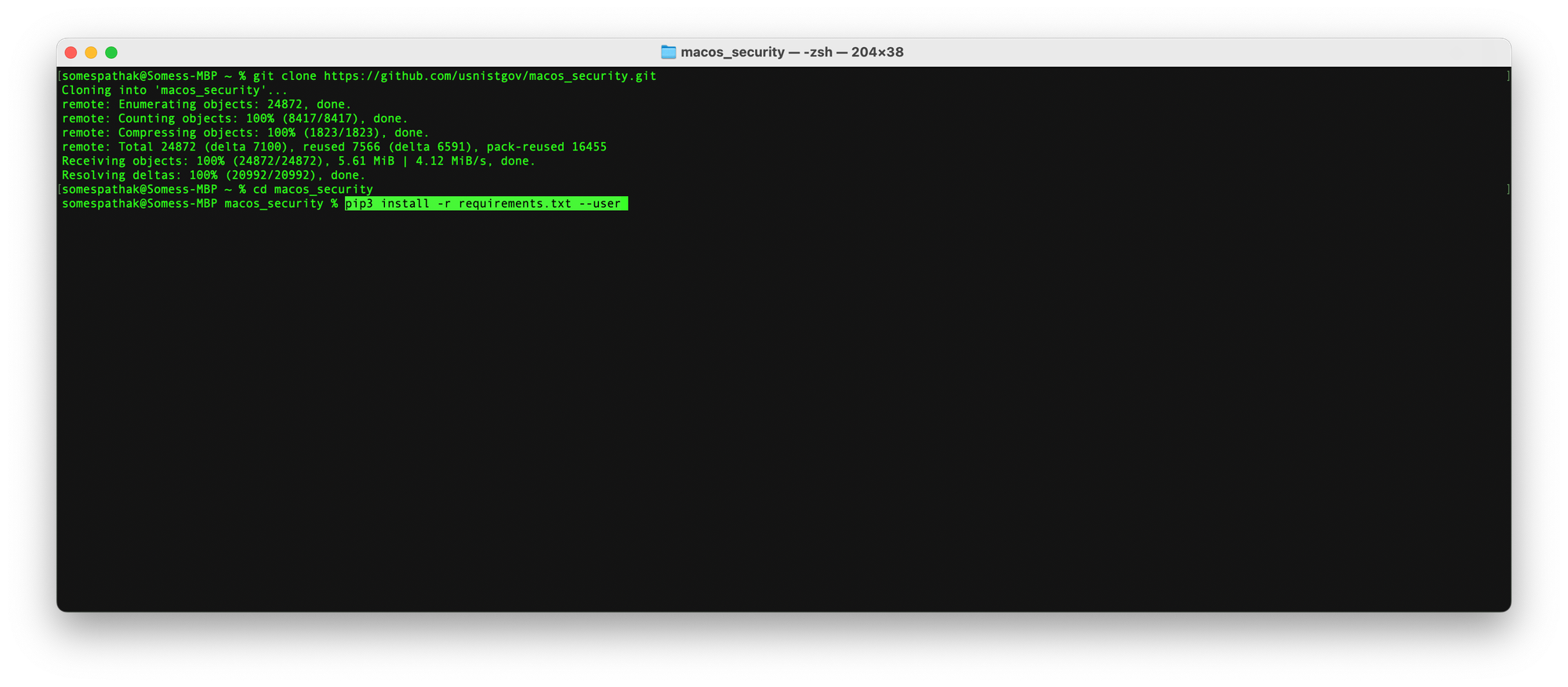
bundle install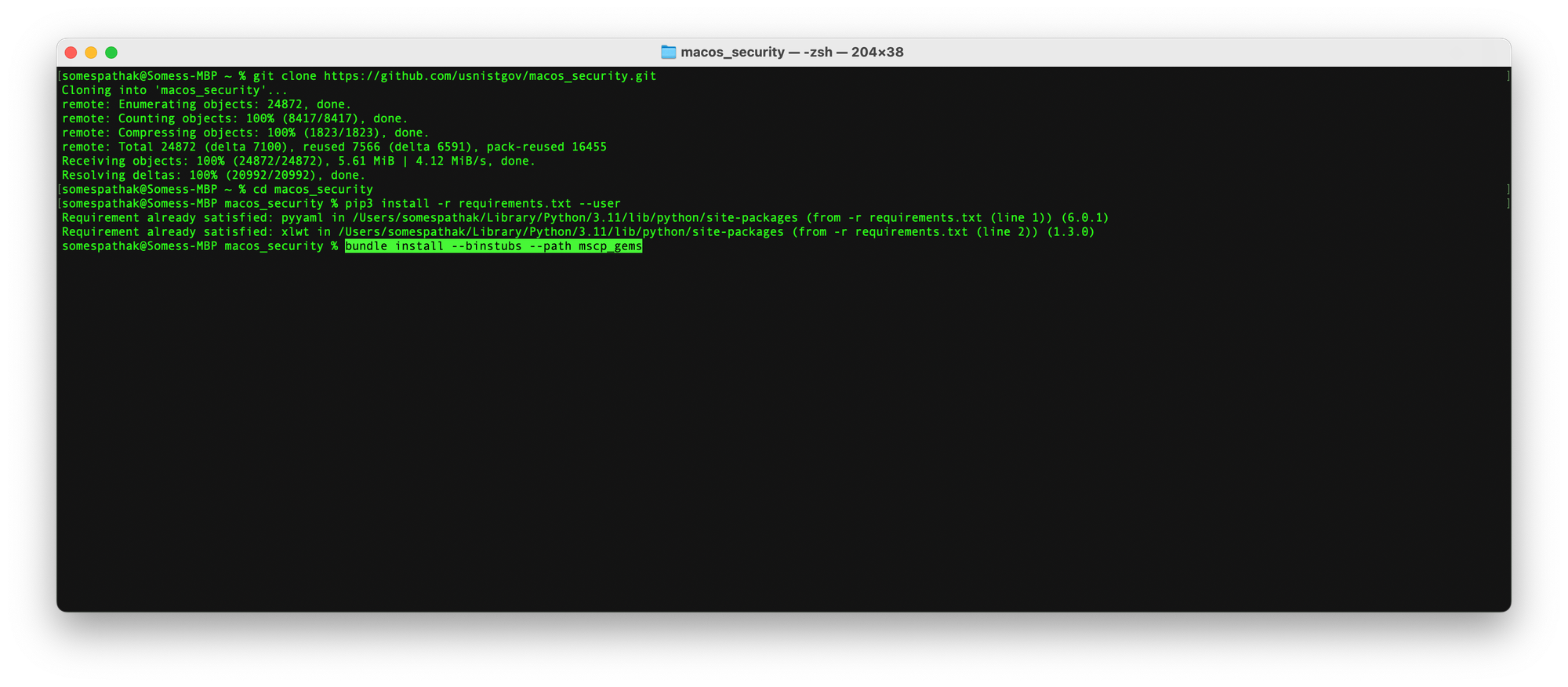
After you’ve cloned the mSCP repository to your Mac and installed the required software, you can explore the mSCP components. You can view the files in the cloned repository using the text editor of your choice.
open ./
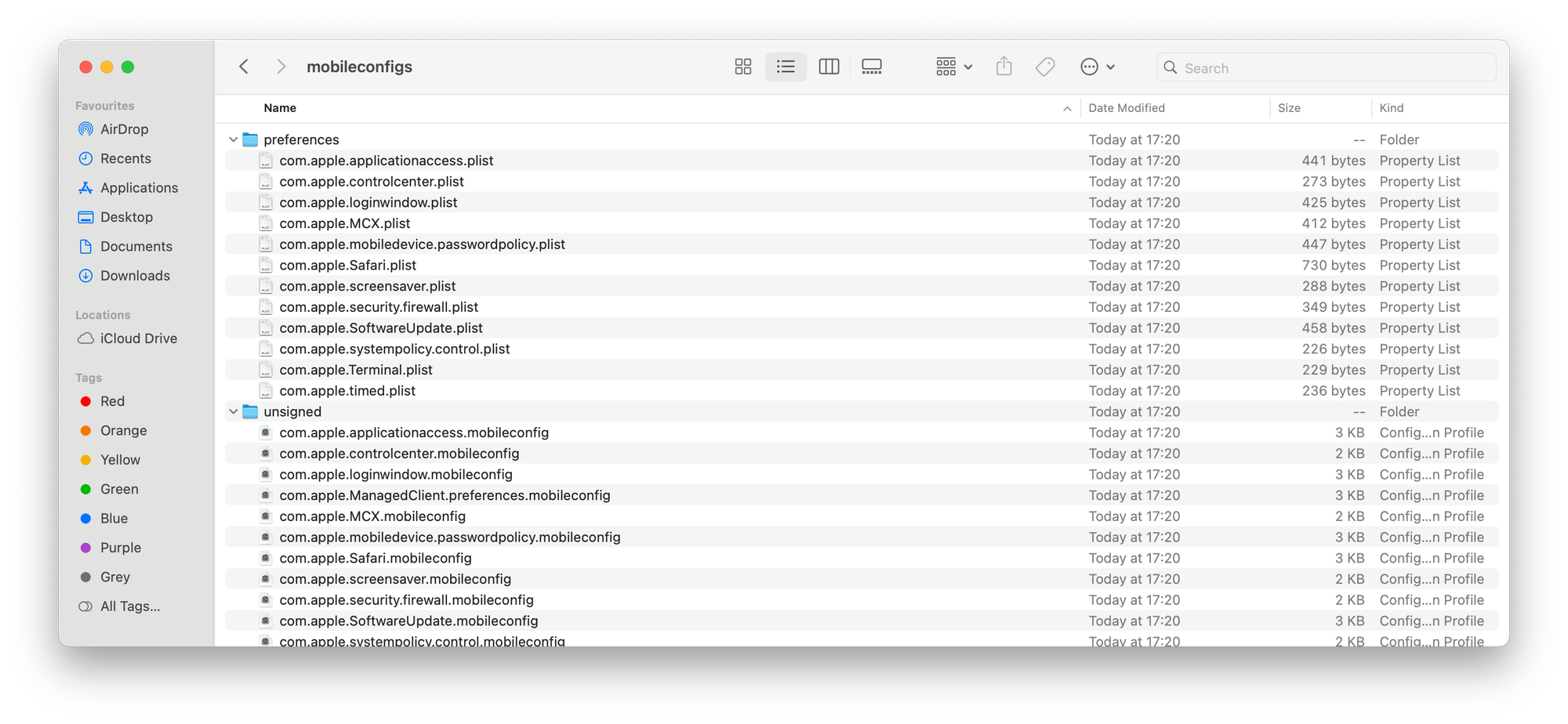
mSCP offers a library of files stored in a format called YAML. These files, located in the "rules" folder, connect to specific compliance requirements outlined in various security guides and policies. You can view and even edit these YAML files using most code editors, like Xcode or BBEdit.
Each file is organized into specific sections, containing key information needed to build and deploy security baselines for your Mac devices. These sections are already filled with appropriate configurations to get you started. The following table breaks down the purpose of each section within the YAML files.
Security baselines are essentially recipes for keeping your Macs safe. Each recipe utilizes specific ingredients, represented by individual security rules. These rules come with labels, known as metadata tags, that identify which recipes (baselines) they belong to.
Creating these recipes is where the generate_baseline.py script comes into play. This script acts as a special program you can run to search through a collection of pre-defined security rules. You simply tell it a keyword (like "encryption" or "network access"), and the script finds all the rules related to that keyword.
Using those matching rules, the script then creates a customized "security recipe" for you. This recipe, saved as a .yaml file, outlines the specific security settings you need to implement on your Macs. This simplifies documenting and enforcing the desired security posture across your entire fleet. Essentially, the script does all the heavy lifting by finding the ingredients (rules) and putting them together in a clear recipe (baseline) for you. You can find this script within the "scripts" folder of the project you downloaded.
cd macos_security./scripts/generate_baseline.py -l
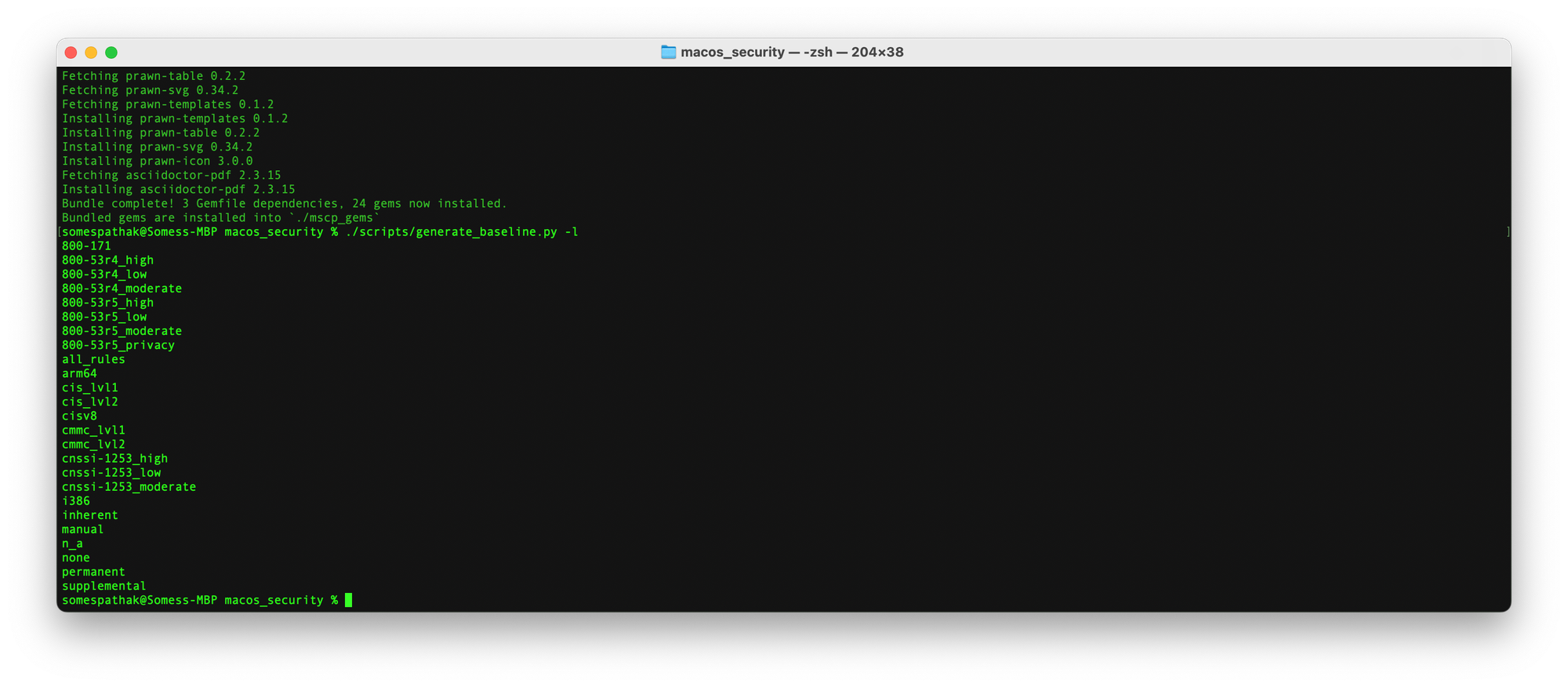
cis_lvl1 baseline
mSCP allows you to take your YAML security rules and transform them into practical instructions for your Mac environment. This process involves a helpful Python script named generate_guidance.py.
cd command (change directory) to navigate to the directory containing your mSCP files. For example, if you downloaded mSCP to your Downloads folder, you would type cd Downloads/macos_security ./scripts/generate_guidance.py -p -s baselines/cis_lvl1.yaml
-p: This flag tells the script to generate configuration profiles and PLIST files (special Mac settings files). -s: This flag instructs the script to create a script for compliance checking. This script helps you verify if your Macs adhere to your security guidelines.baselines/cis_lvl1.yaml: This part specifies the location of your security baseline file. You can replace cis_lvl1.yaml with the actual filename of your baseline.Once the script finishes running, open Finder and navigate back to the macos_security directory. You'll find a new folder named after your baseline (e.g., cis_lvl1). This folder contains all the generated files, including configuration profiles, compliance checking scripts, and human-readable security guidance documents.
While this tutorial won't cover customizing baselines in detail, it's valuable to know how to tailor them to your organization's specific security requirements.
The pre-populated configurations in the baseline files are a good starting point. If unsure about a specific field, it's best to consult the mSCP documentation or seek guidance from a security professional.
Here's the basic idea:
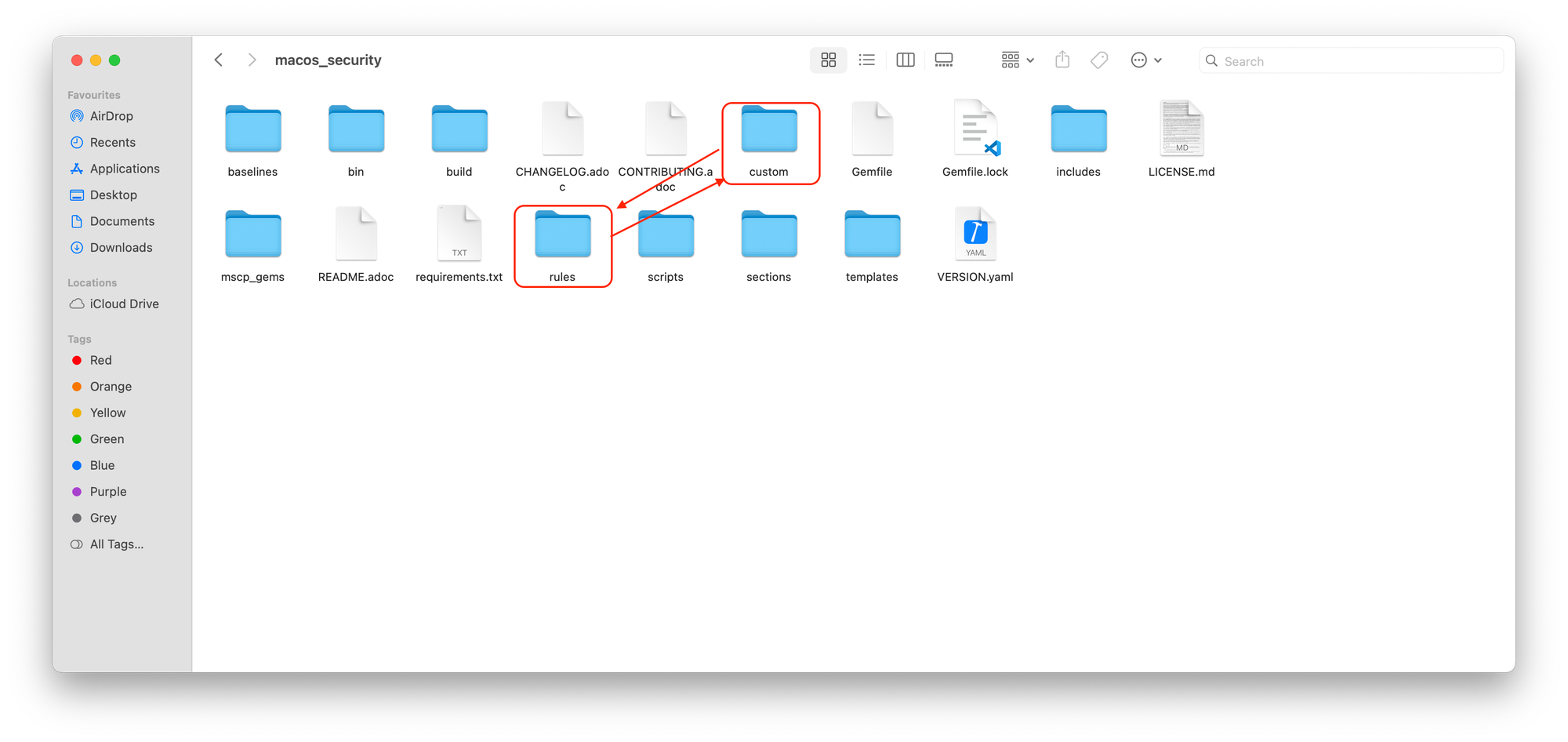
The provided screenshot (not included here) likely shows the rule file "system_settings_time_server_configure.yaml" opened in Xcode. In this example, you'll see that the time server has been set to "time.apple.com." This represents the specific setting being modified within the rule.
Technical Jargon Explained:
By following these steps and understanding the example, you can confidently customize existing security rules in mSCP to create a robust security posture tailored to your organization's needs.
Once you've generated baseline files using mSCP, you can leverage them to create a comprehensive baseline within Microsoft Intune. This baseline will consist of three key components:
Profiles: Remember the command you ran earlier to generate guidance? This command not only created human-readable documents but also produced two crucial files:
../build/{baseline}/preferencesdirectory. It allows you to set exemptions to specific security rules based on your company's unique policies. Think of it as an exception list for security settings.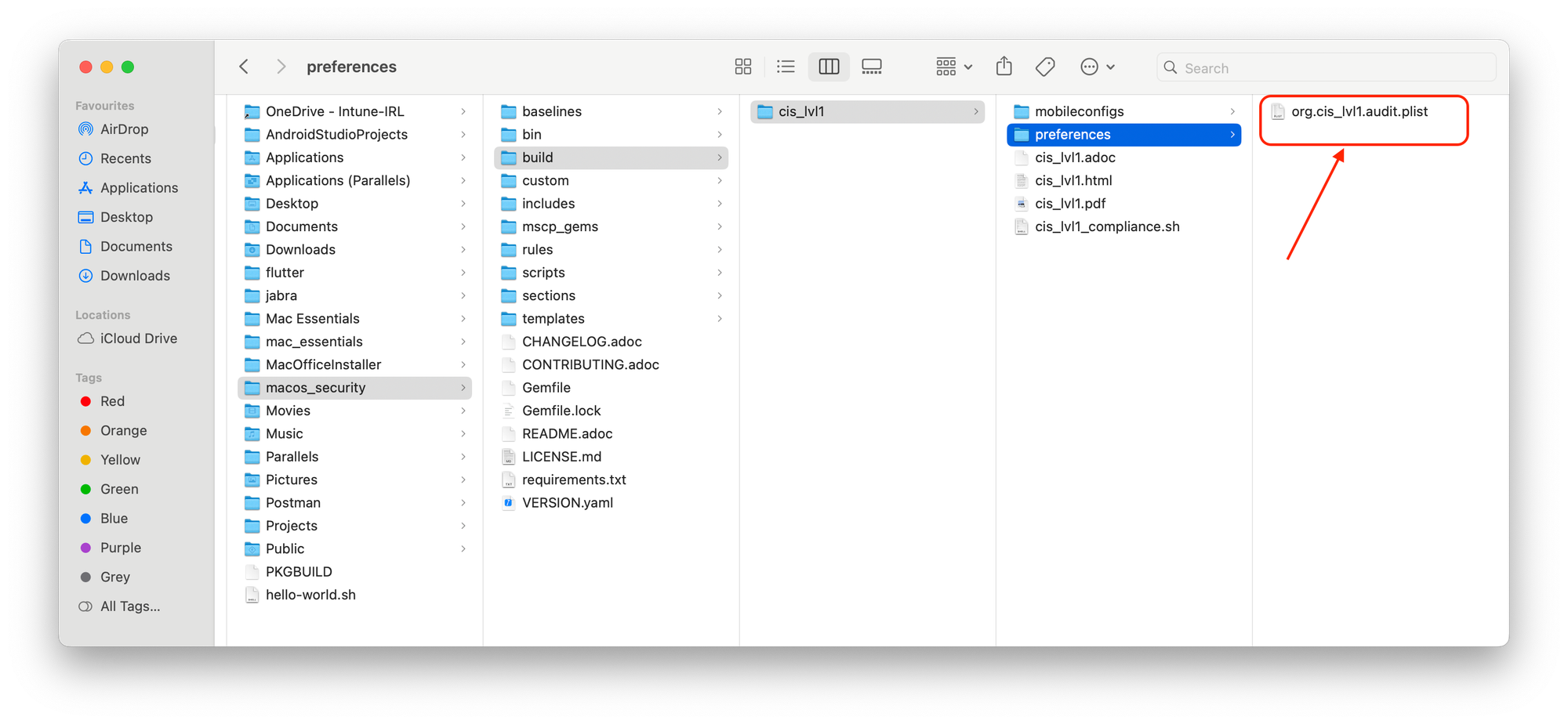
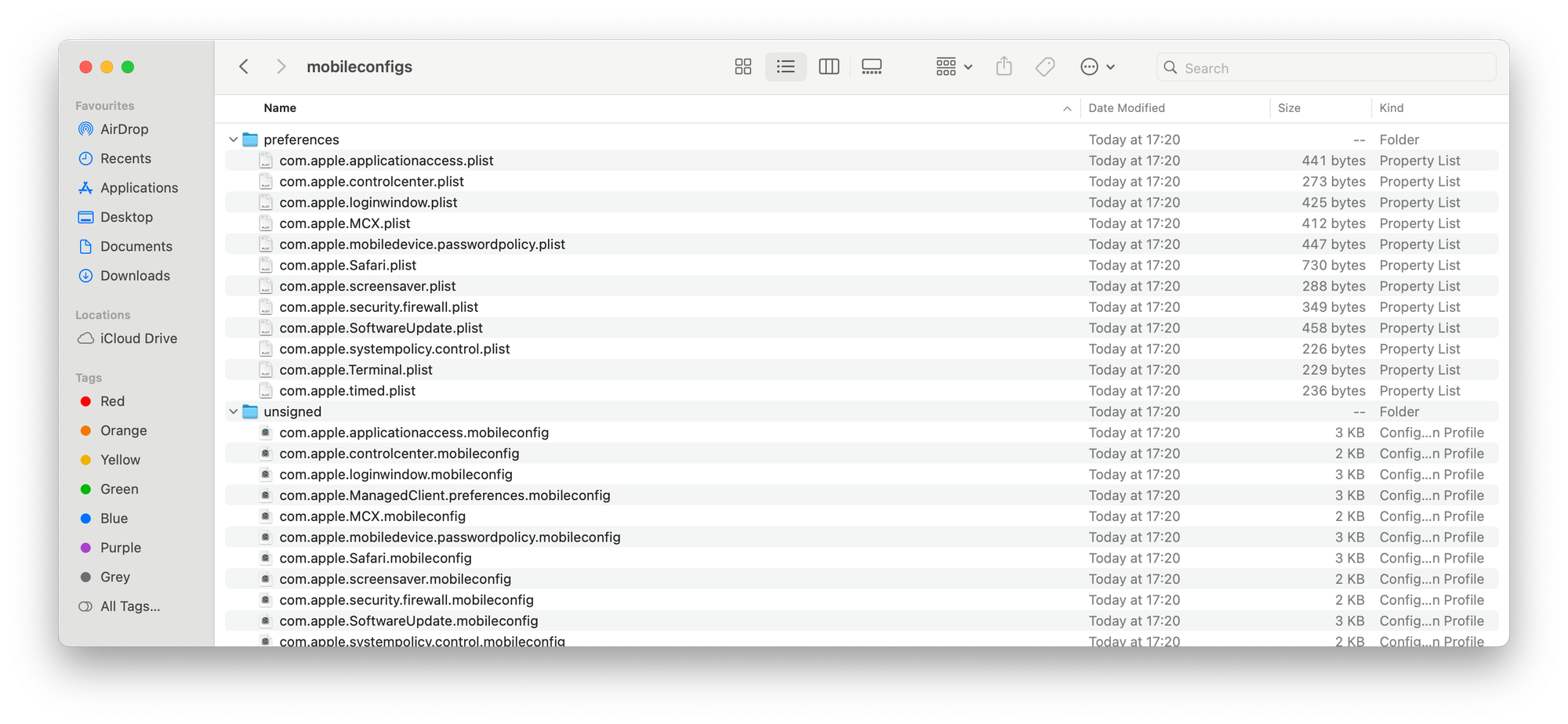
Scripts: mSCP also generates a compliance script located in ../build/{baseline}/{baseline}_compliance.sh. This script plays a vital role:
By combining these components (profiles, audit PLIST, and compliance script), you can establish a robust and automated security baseline for your Macs managed through Intune. This ensures your devices consistently maintain the desired security posture as defined by your organization's policies.
Once you've generated the security baseline components using mSCP, it's time to leverage them within Microsoft Intune to enforce the desired security posture on your Macs. Here's a step-by-step guide for each element:
1. Deploying Baselines (.mobileconfig Files):
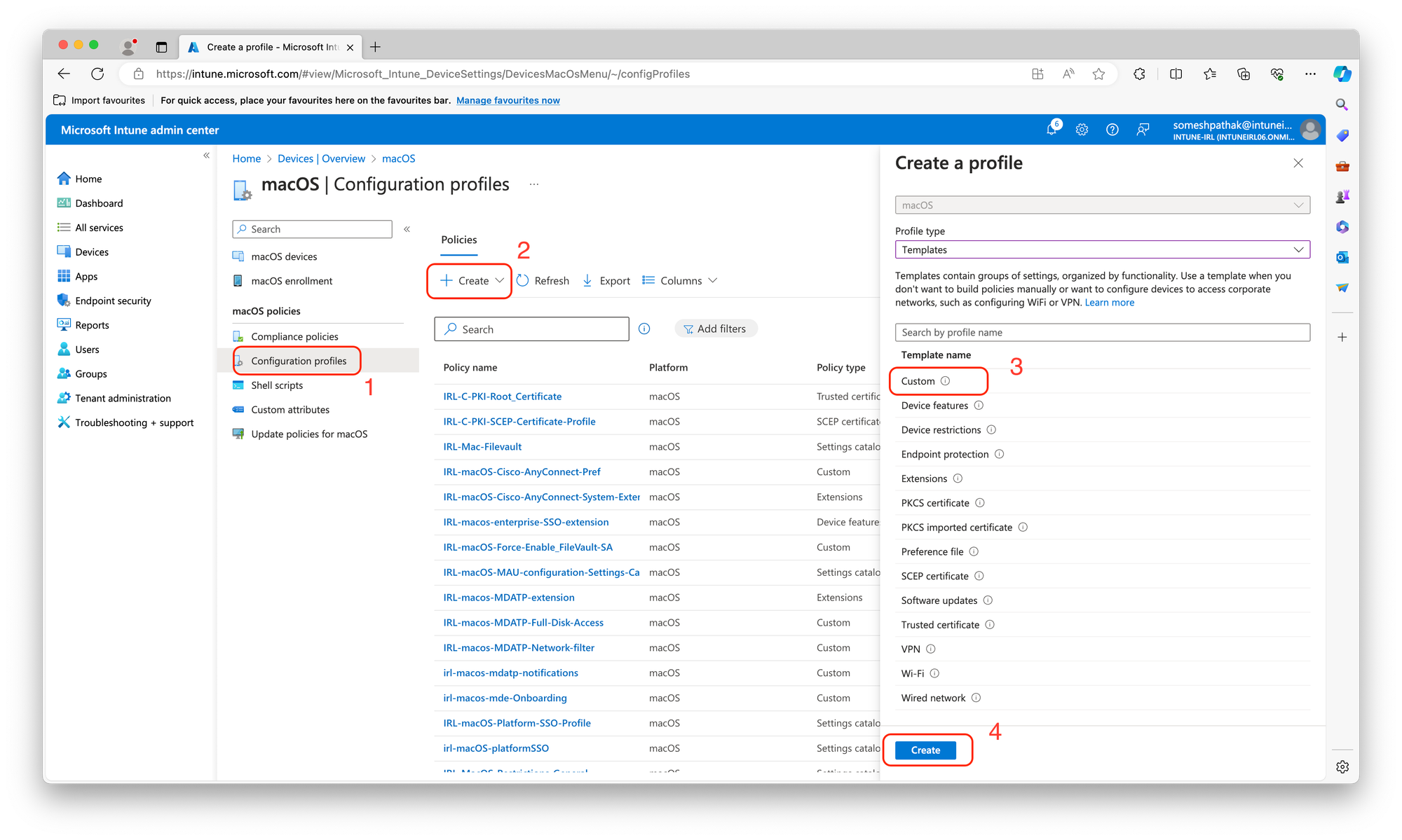
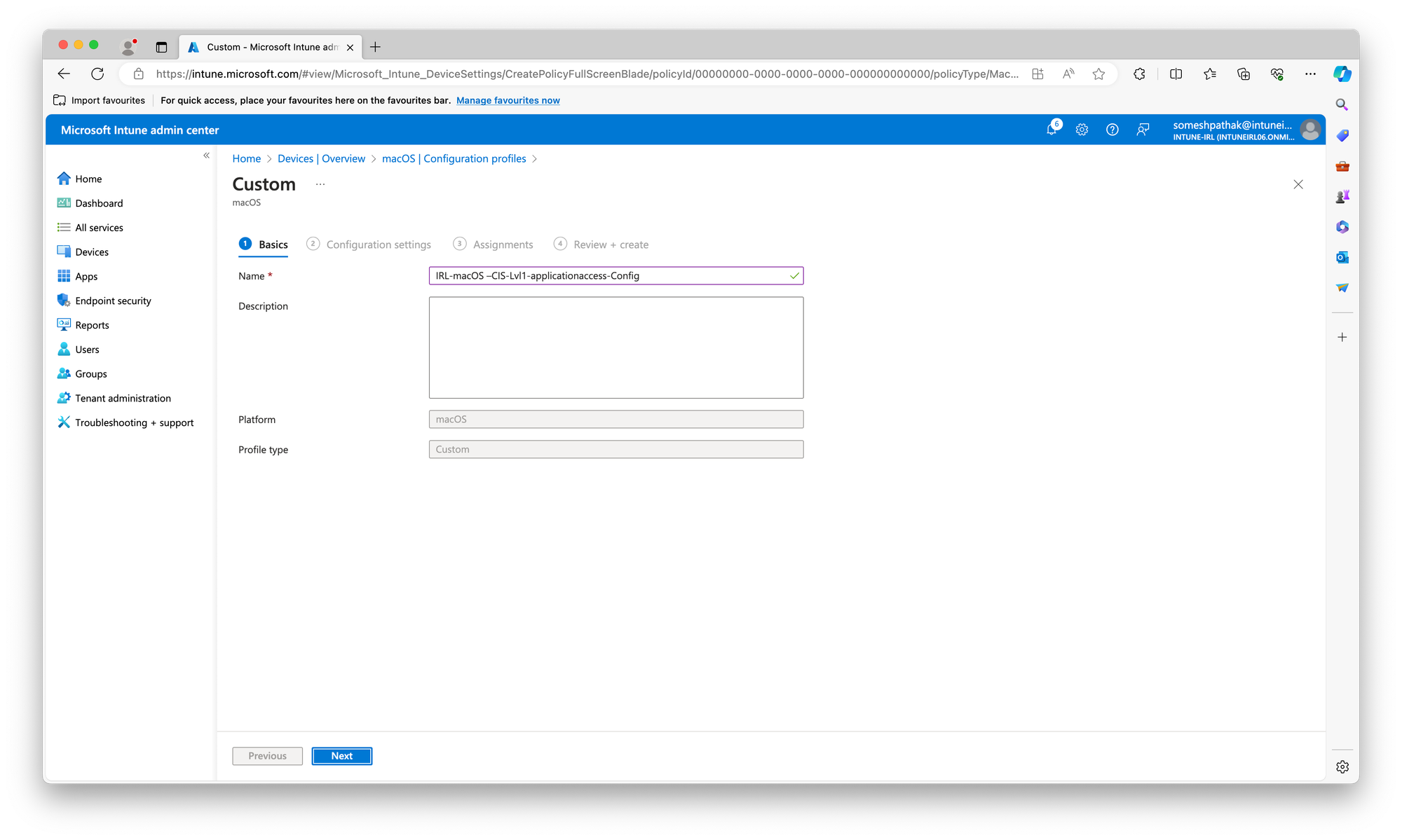
../build/{baseline}/ directory (replace {baseline} with your actual baseline name).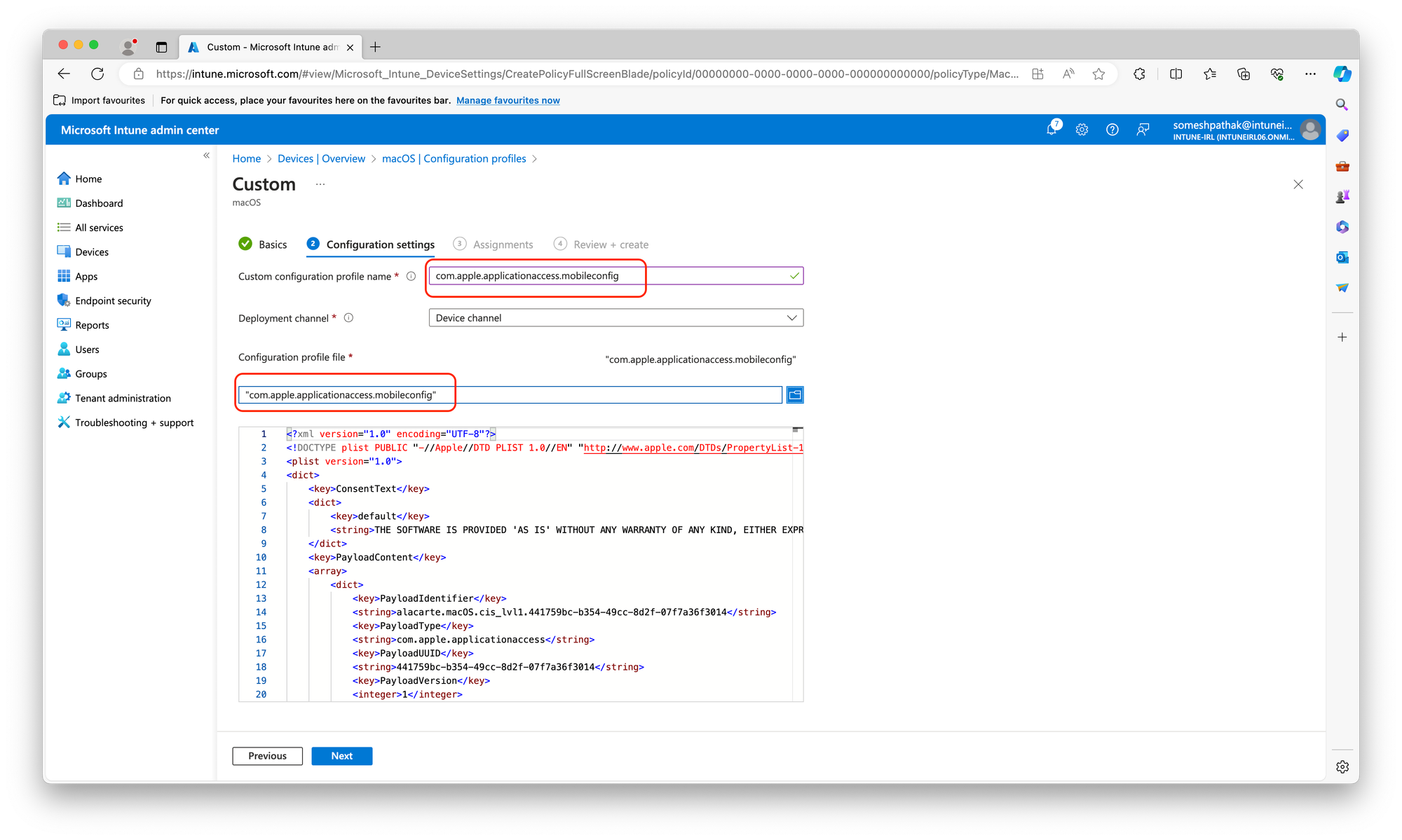
2. Deploying Baseline Compliance Script:
../build/{baseline}/{baseline}_compliance.sh.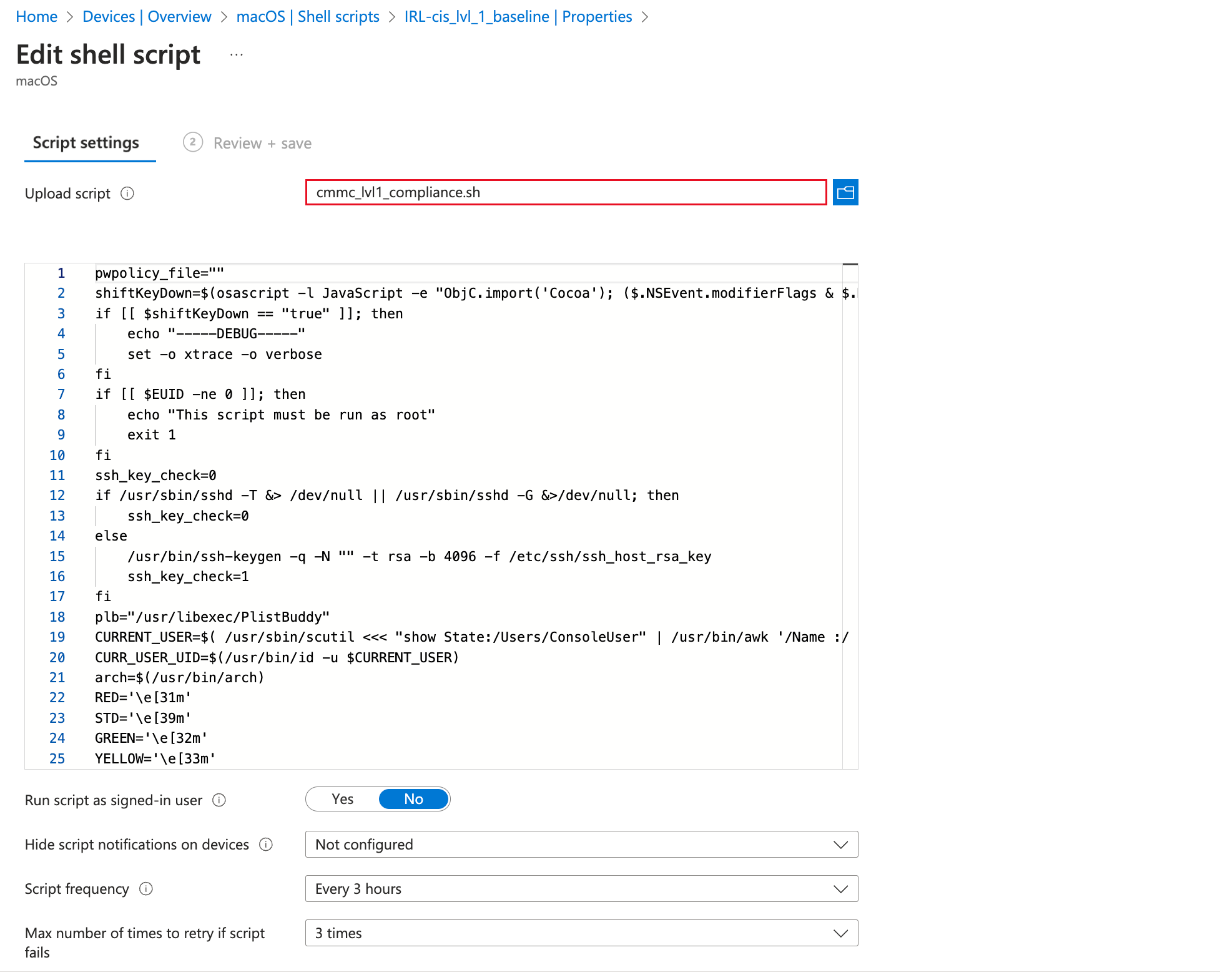
3. Deploying Audit PLIST:
This step allows exemptions defined in the audit PLIST file to be utilized.
../build/{baseline}/preferences/{audit_plist_filename}.plist). 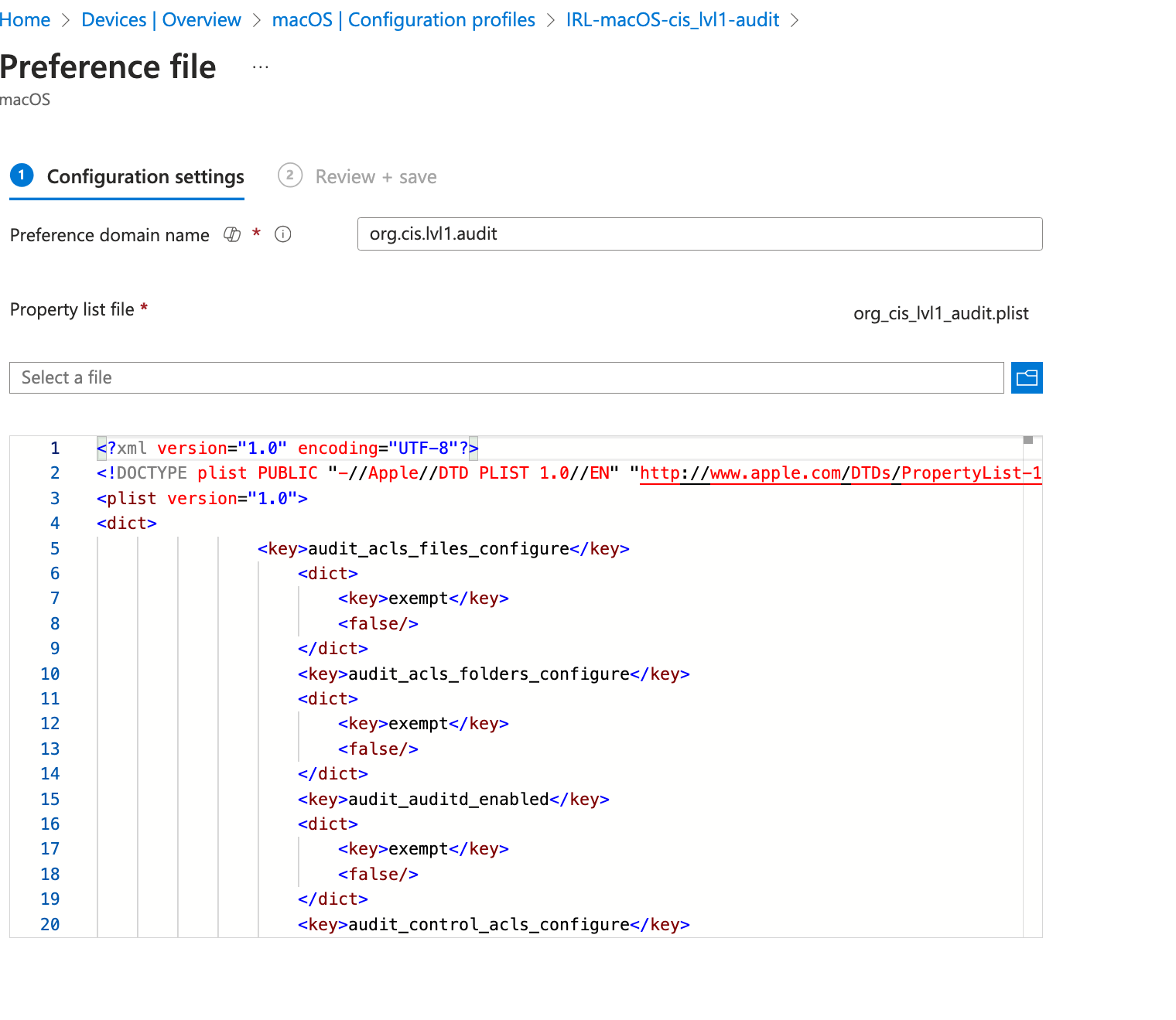
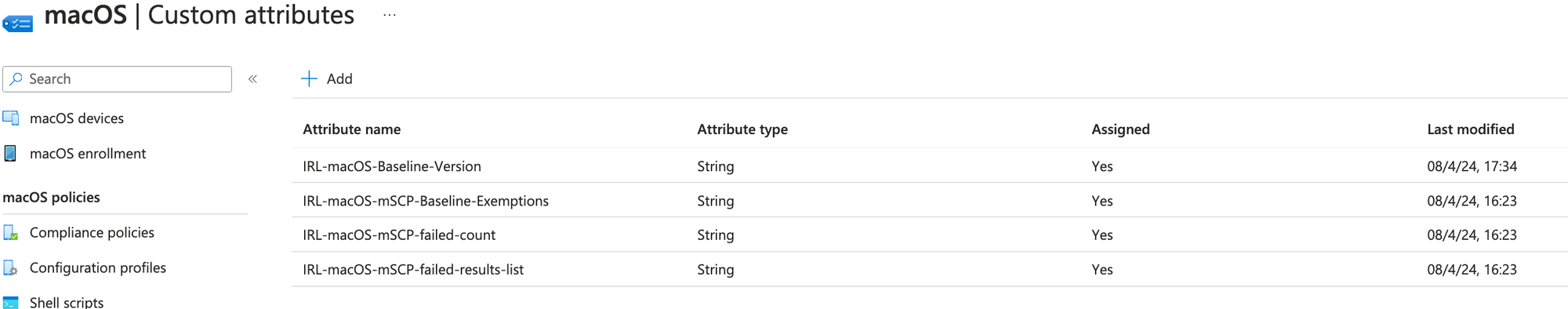
4. Deploying Custom Attributes:
This section explores deploying custom attributes for reporting purposes and we will be creating the below 4 custom attributes:
By following these steps and referring to the provided resources for optional configurations, you can effectively deploy the various components of your mSCP-generated security baseline within Intune. This will establish a centralized and automated security posture, ensuring your Macs adhere to your organization's security policies.
Once you've deployed the security baselines generated by mSCP using Intune, you'll gain a newfound sense of control and visibility. Intune provides a user-friendly interface that allows you, the IT admin, to see at a glance the security posture of your entire Mac fleet.
Imagine a dashboard where you can see:
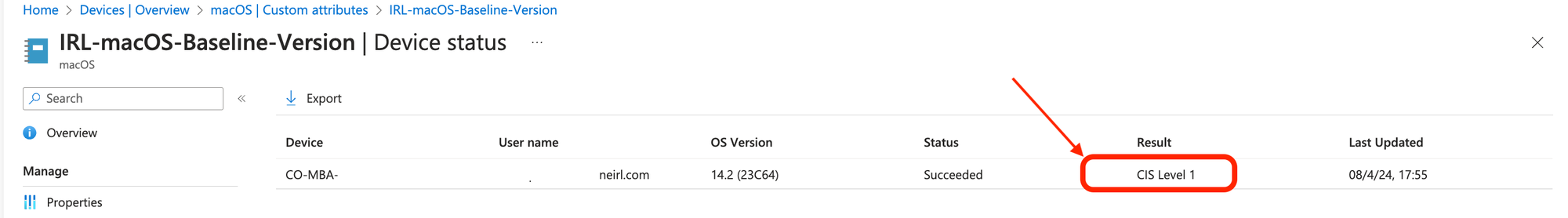
This centralized view empowers you to easily identify Macs that:
By leveraging mSCP and Intune, you gain a clear and concise picture of your Mac security landscape. This allows you to take proactive measures to:
This newfound visibility translates to peace of mind, knowing your Mac data is shielded by a comprehensive and well-managed security strategy.
mSCP empowers you to craft robust security baselines specifically for your Macs. With a few clicks in Intune, you can effortlessly deploy these baselines to your entire fleet. Intune's user-friendly interface provides a centralized view of your Mac security posture, allowing you to identify missing baselines, outdated configurations, and potential deployment errors. Optional features like automated compliance checks and detailed reporting offer even deeper insights. By leveraging mSCP and Intune, you gain complete control over Mac security, ensuring your data remains protected and your organization stays secure. Explore mSCP today and experience the power of automated security baselines!