This blog dives deep into the recently launched Cloud PKI, a game-changer for simplifying and automating certificate management within your Intune environment. Farewell, On-Premises PKI! For years, managing on-premises Public Key Infrastructures (PKI) meant juggling complex configurations, laborious manual tasks, and hefty infrastructure costs. Enter Cloud PKI, a game-changer recently

This blog dives deep into the recently launched Cloud PKI, a game-changer for simplifying and automating certificate management within your Intune environment.
For years, managing on-premises Public Key Infrastructures (PKI) meant juggling complex configurations, laborious manual tasks, and hefty infrastructure costs. Enter Cloud PKI, a game-changer recently integrated within Intune. This cloud-based service streamlines and automates certificate management, freeing up valuable resources and enhancing security not limited to:
This guide delves into the advanced integration of Cloud PKI with Intune, aimed at empowering Intune administrators with the knowledge to implement a more secure and efficient management environment.
Deploying Cloud PKI within Microsoft Intune involves a strategic process aimed at enhancing device management and security across your organization. This deployment enables secure communication, authentication, and encryption for devices managed by Intune. Here's a comprehensive breakdown of the deployment process.
Before diving into deployment, it's crucial to grasp what Cloud PKI entails. It is a cloud-based public key infrastructure that simplifies certificate management without the need for extensive on-premises infrastructure. It's ideal for securing communications between your devices and the resources accessed by them.
Microsoft-Managed vs. BYOCA: Decide whether to use Microsoft Cloud PKI or to bring your own CA. Each option has its benefits, with Microsoft-managed offering simplicity and BYOCA offering greater control.
Integrating the Microsoft Cloud PKI with Microsoft Intune simplifies the certificate management process, making it an attractive option for organizations looking to deploy Cloud PKI. This approach leverages Microsoft's infrastructure to issue and manage certificates, reducing the complexity and maintenance overhead for your organization. Here's how to get started with configuring the Microsoft Cloud PKI in Intune:
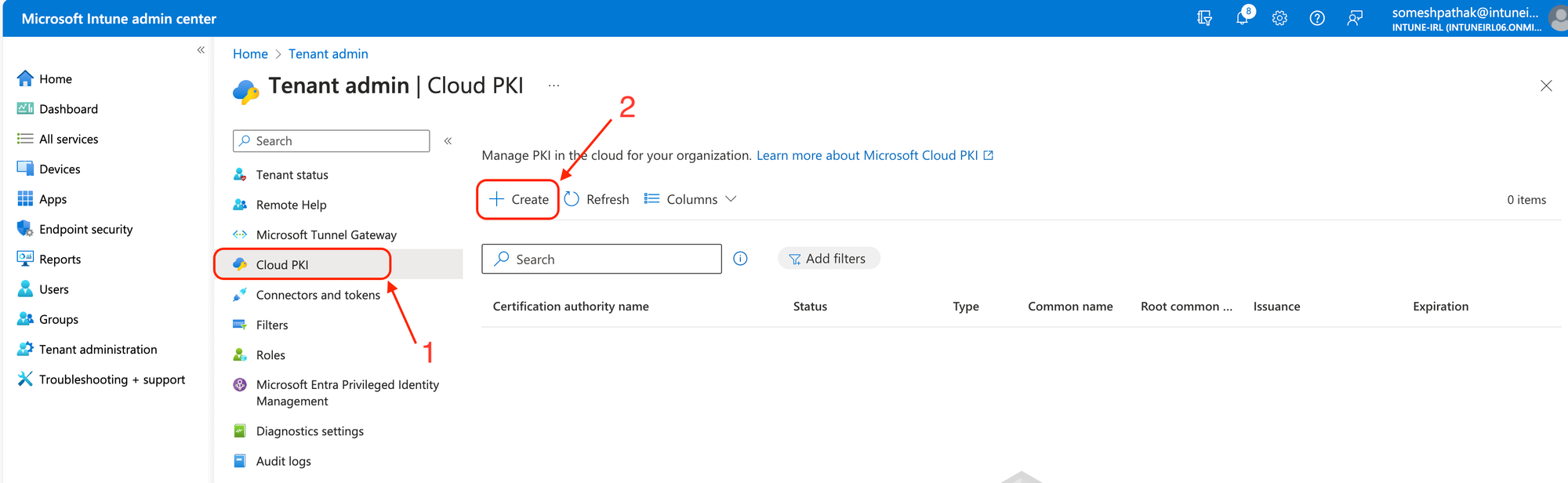
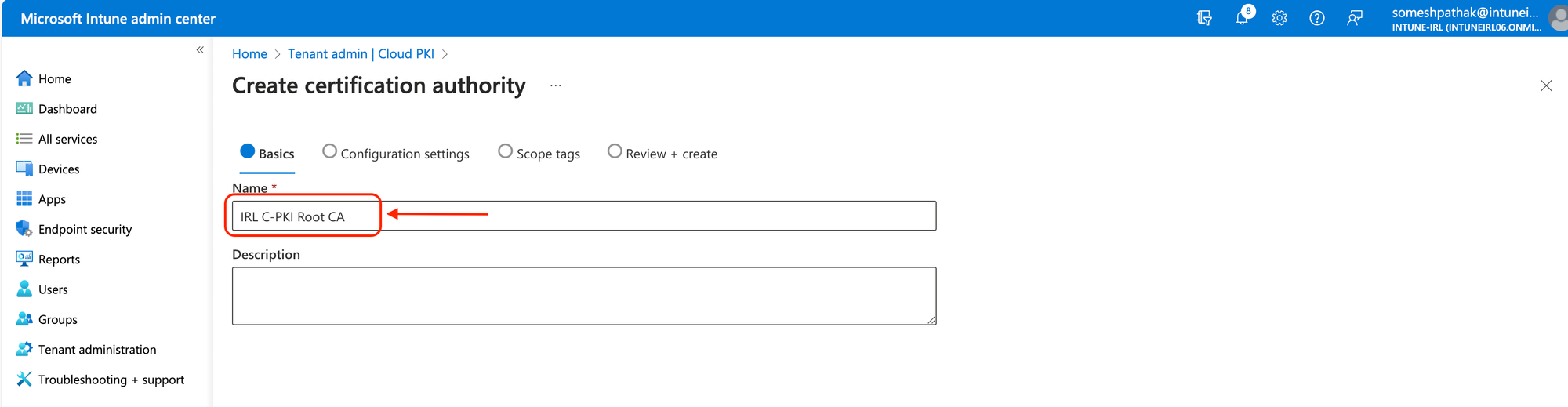
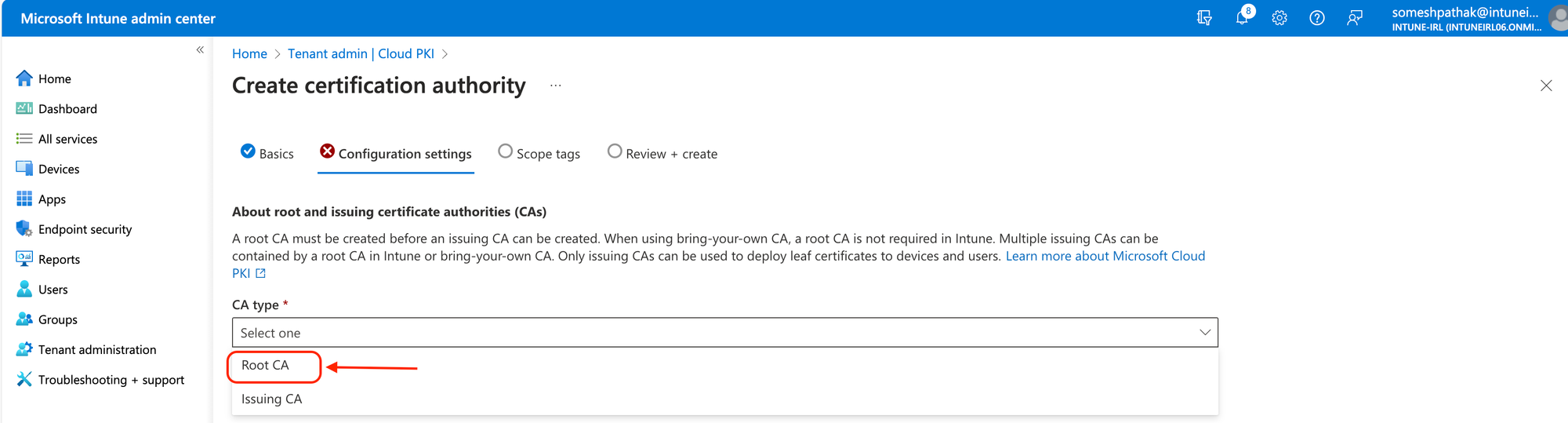
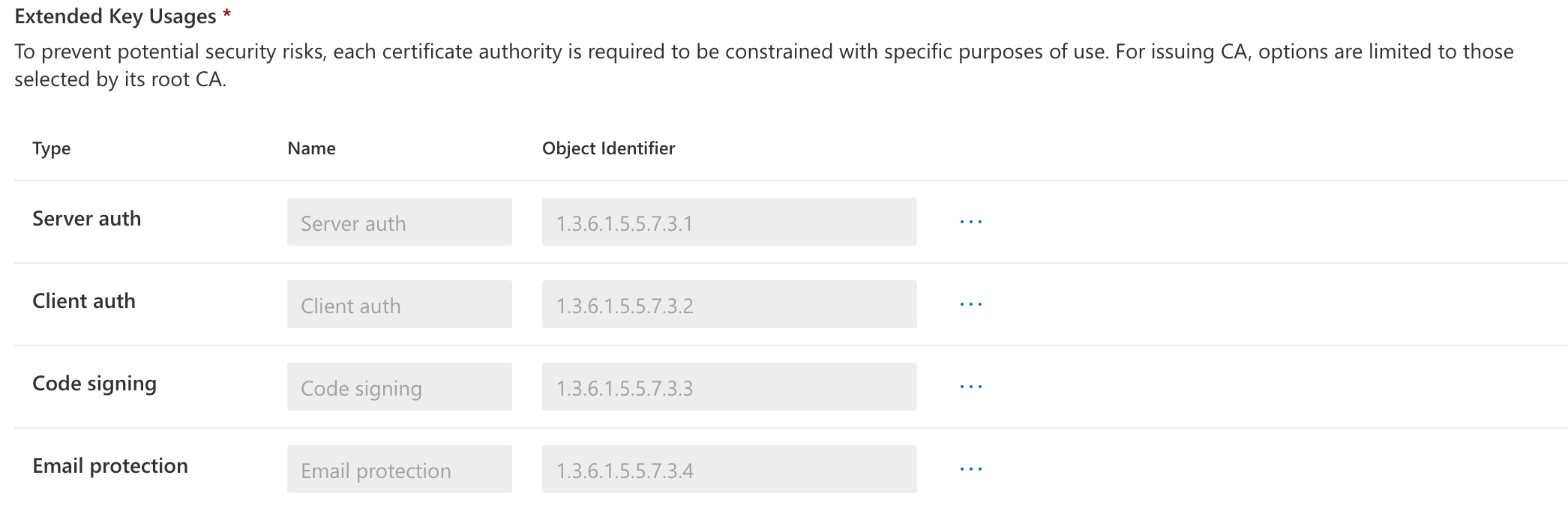


For Intune-managed devices, certificates must be issued by an issuing CA. A SCEP service that serves as a certificate registration authority is automatically provided by Cloud PKI. Using a SCEP profile, it makes certifications requests on behalf of Intune-managed devices to the issuing CA.
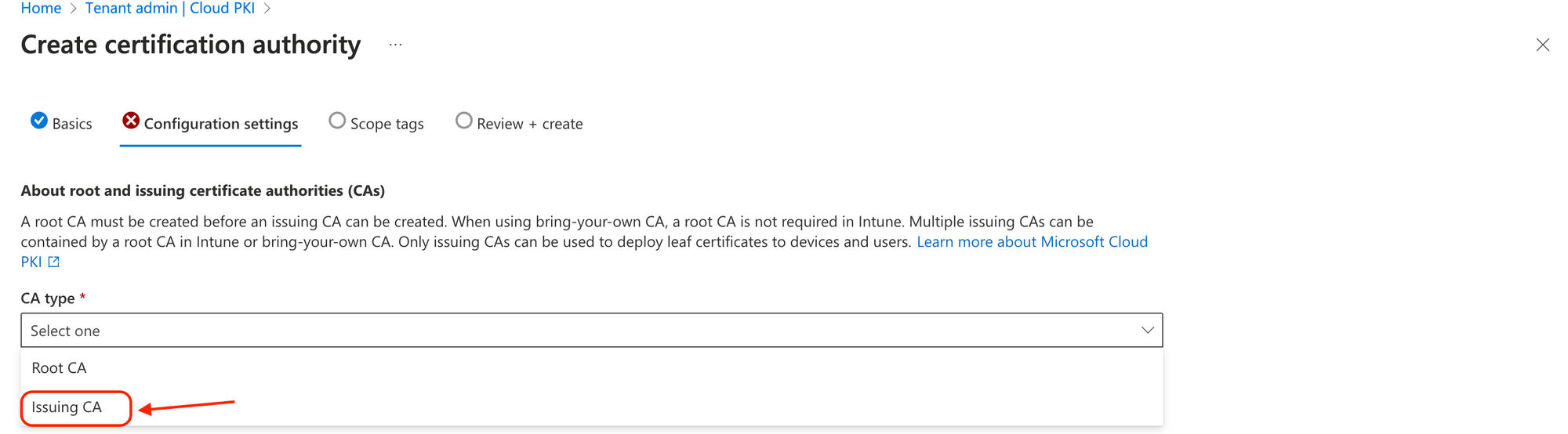
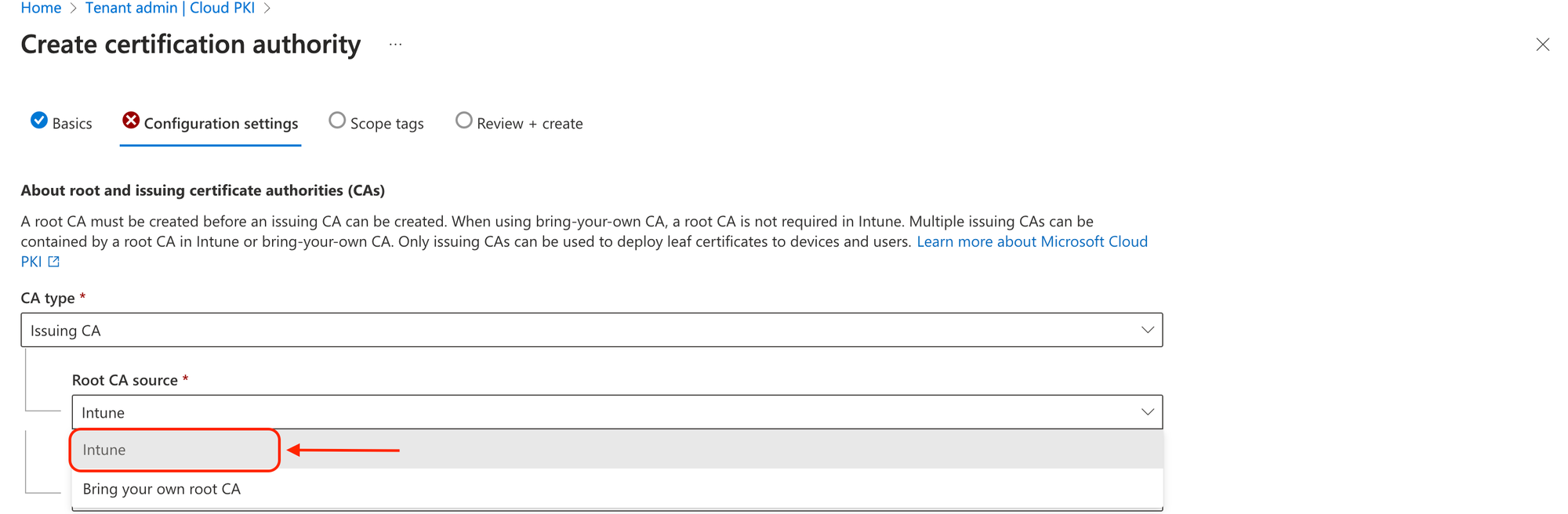
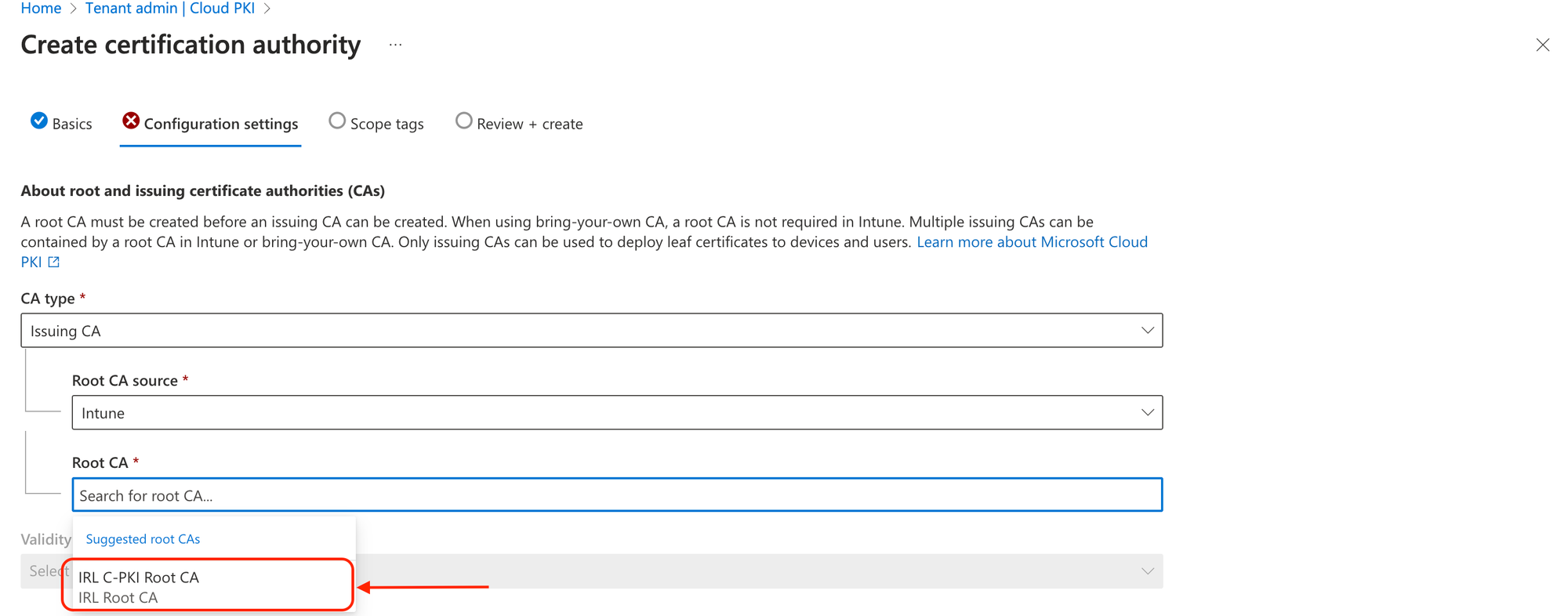
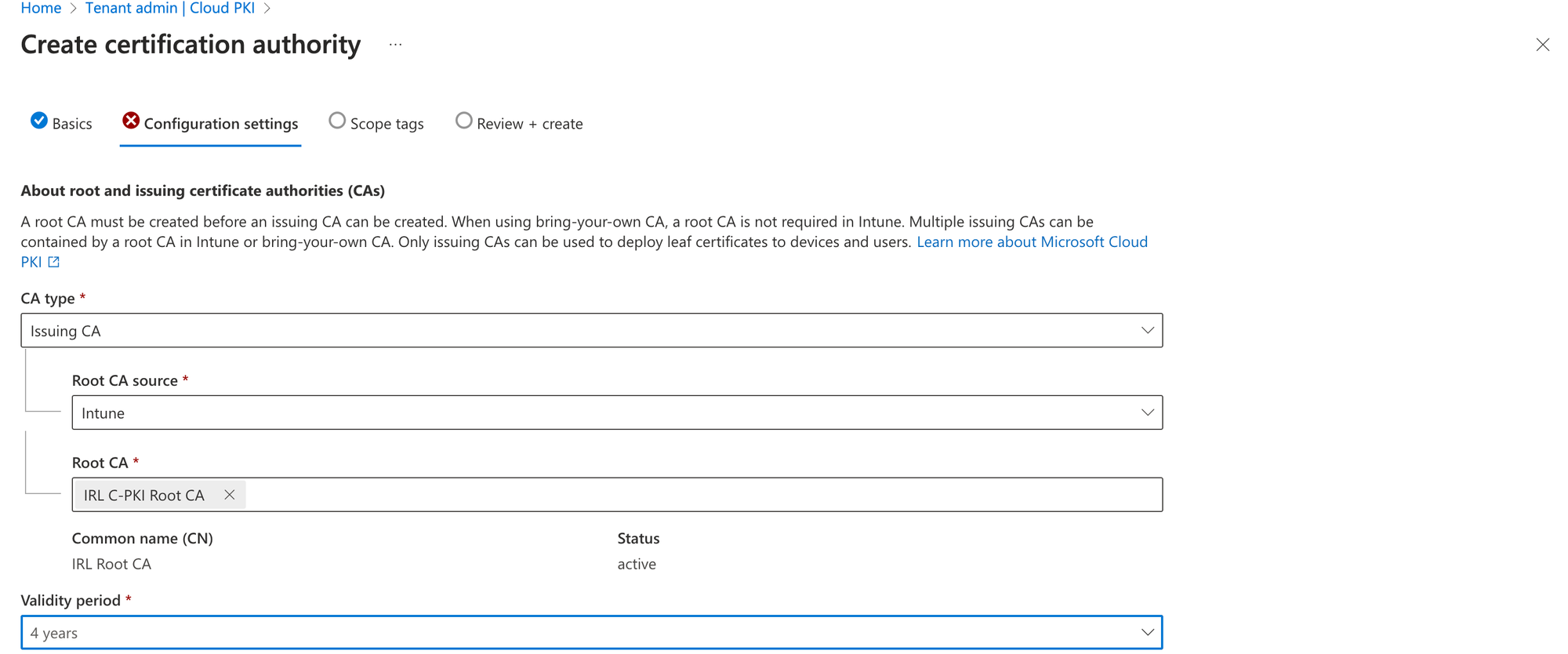
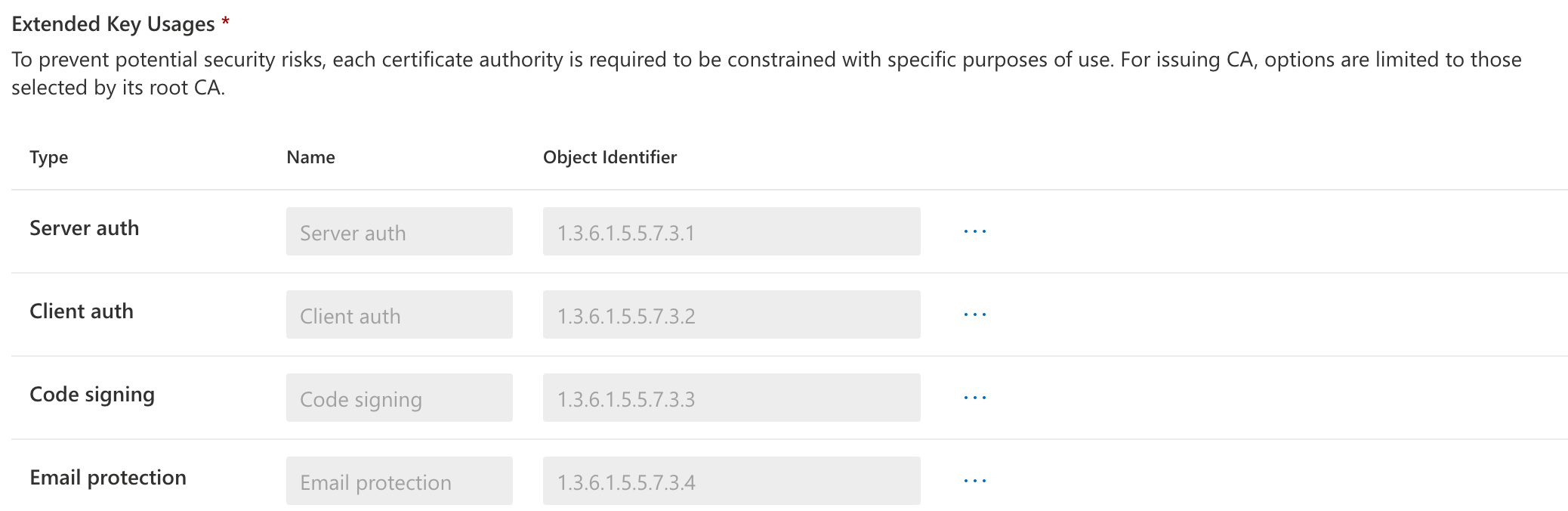

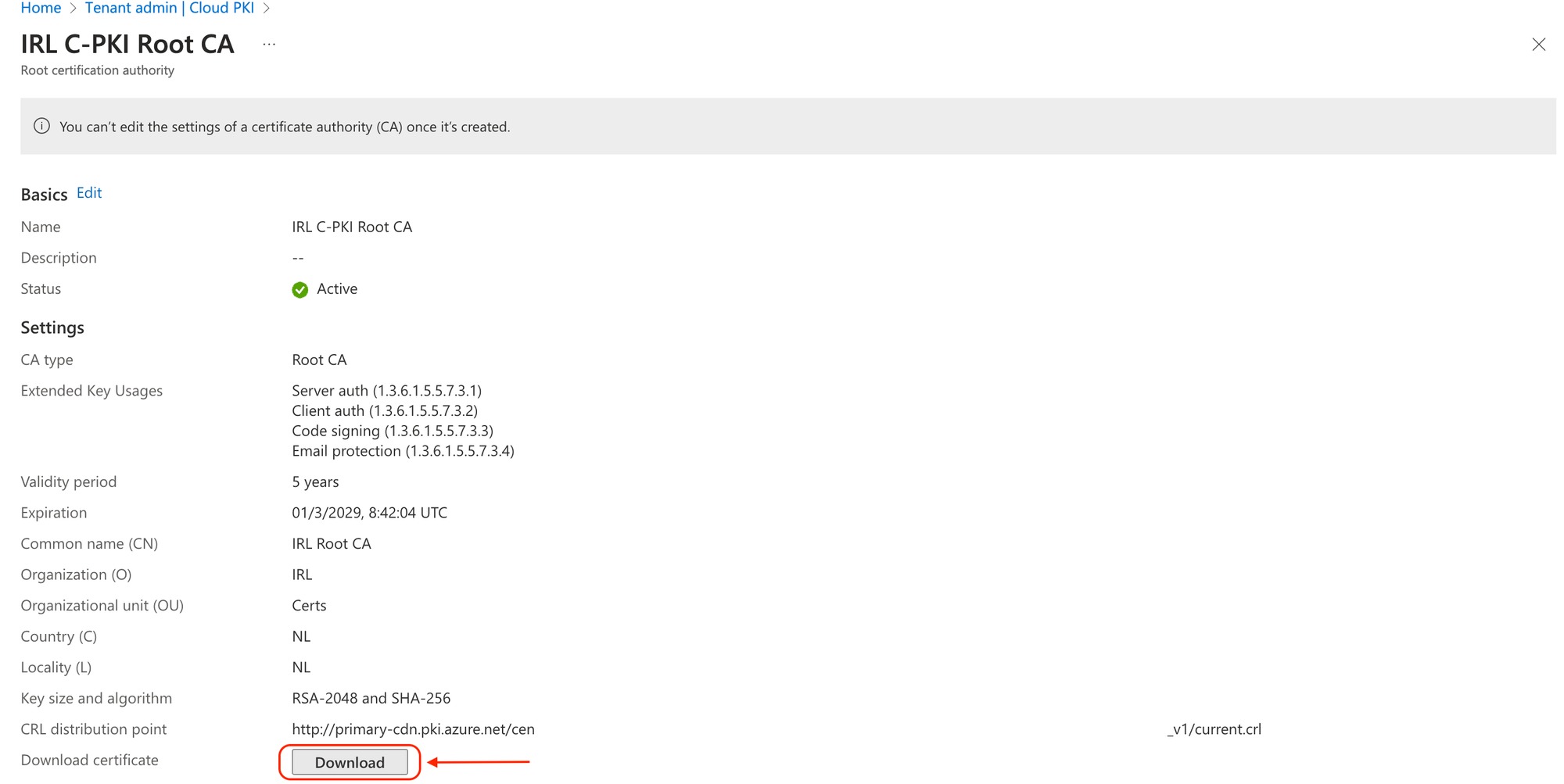
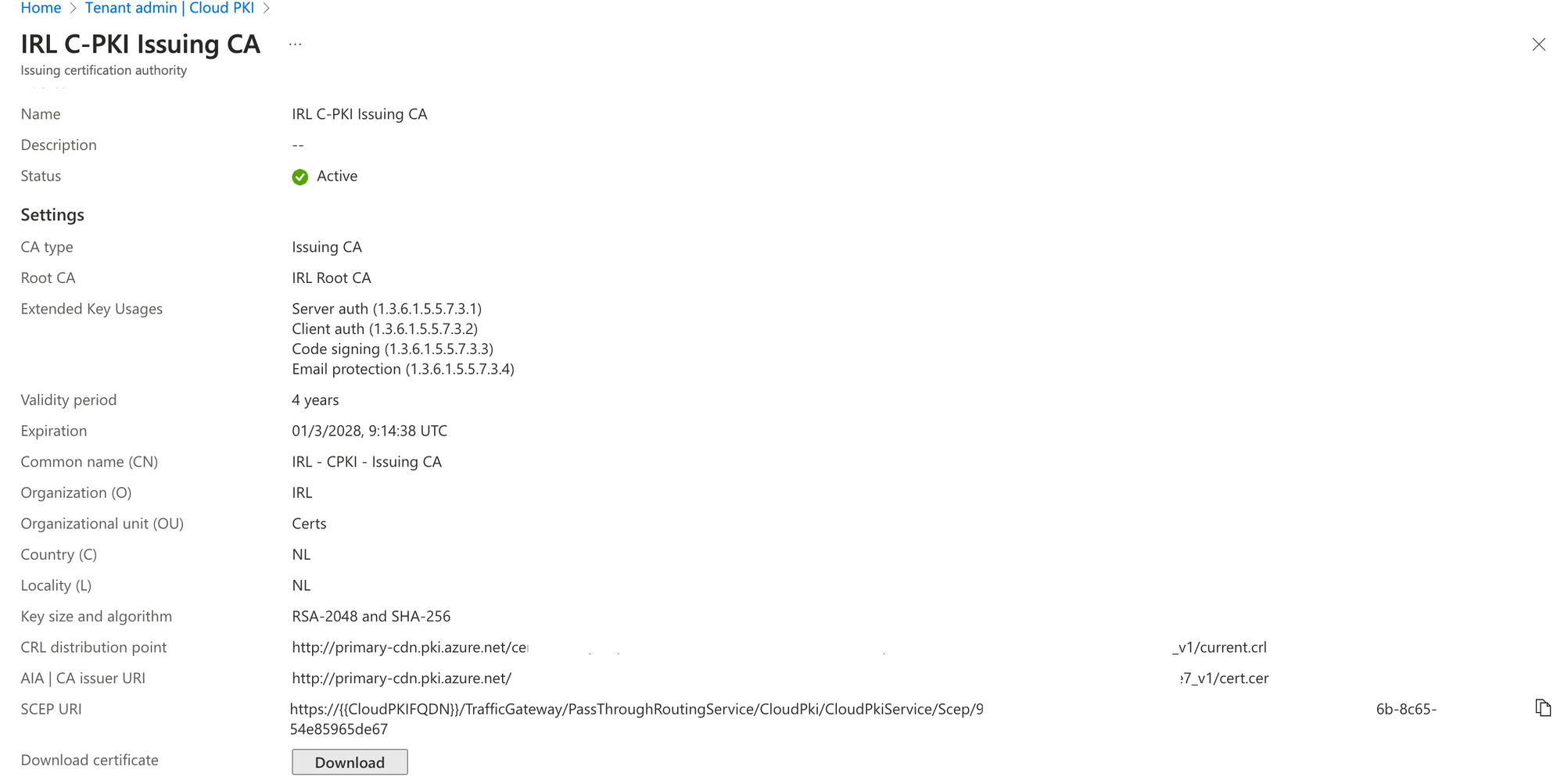
You need the public keys for both issuing and root CA certificates in order to build the trusted certificate profile needed for Cloud PKI. When requesting a certificate using SCEP certificate profiles, the public keys create a chain of trust between Intune managed devices and Cloud PKI. To download the public keys for these certificates, select Download.
For the root CA:
For the issuing CA:
Create one trusted certificate profile for the root CA certificate and one for the issuing CA.
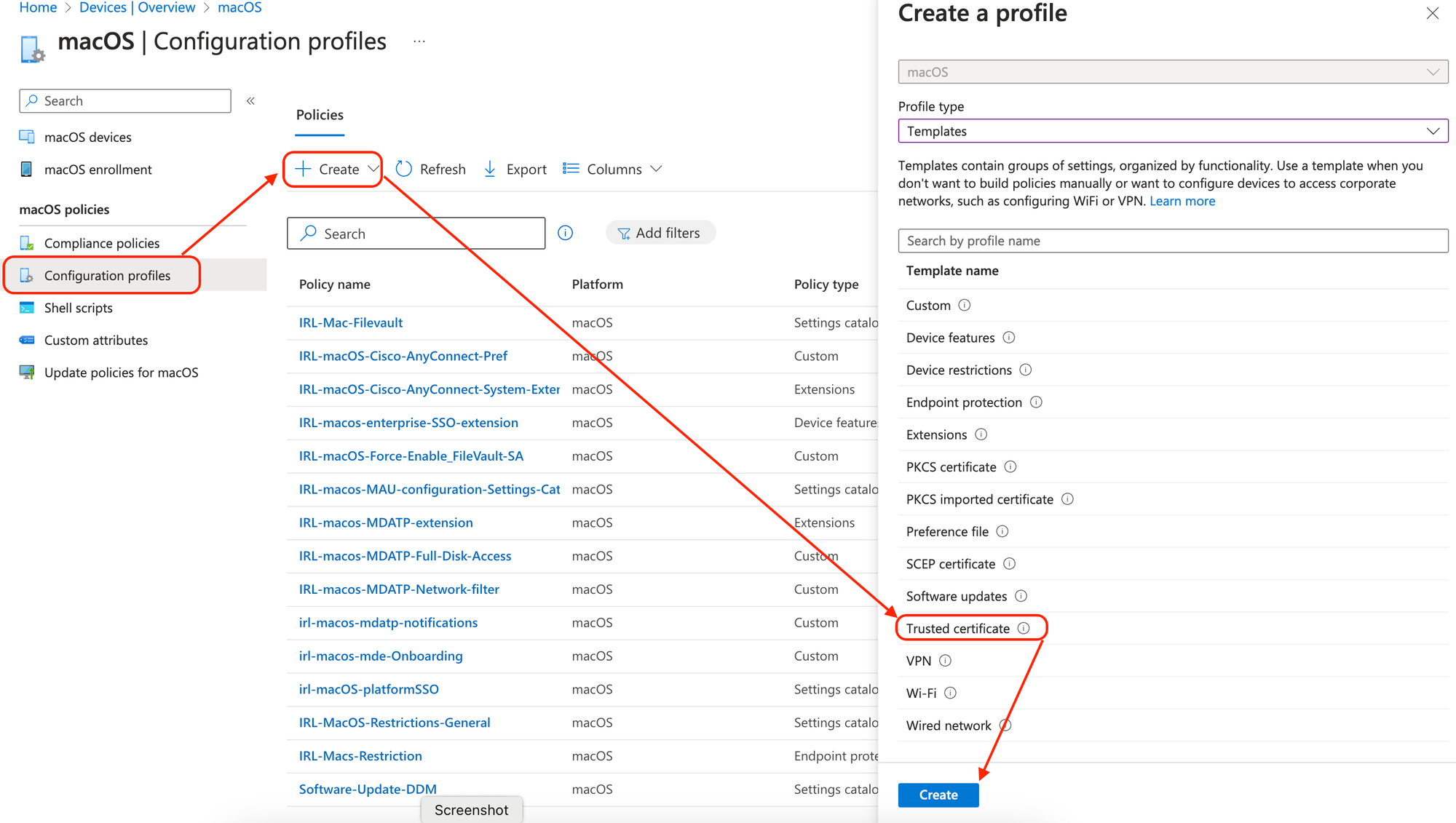
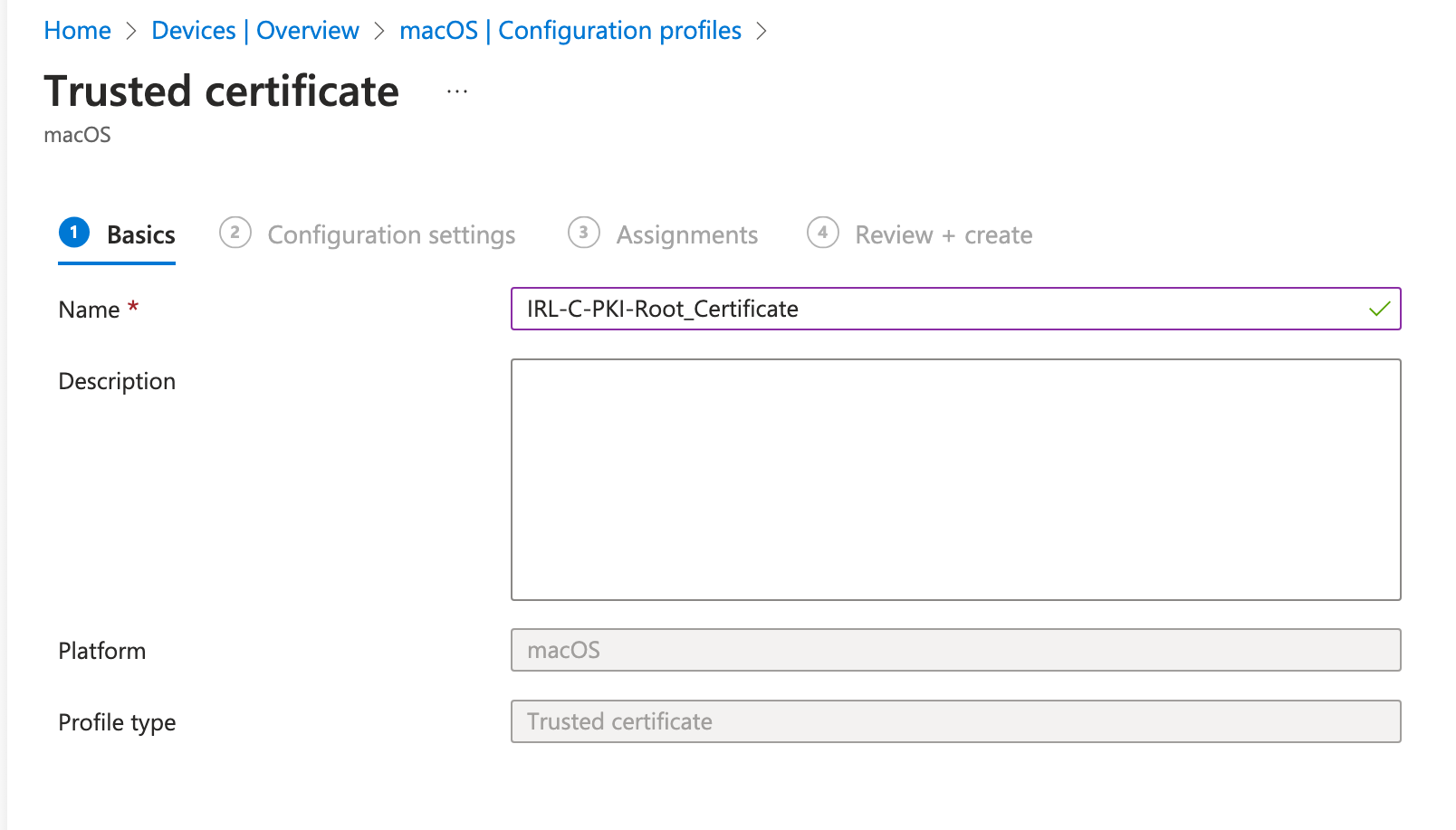
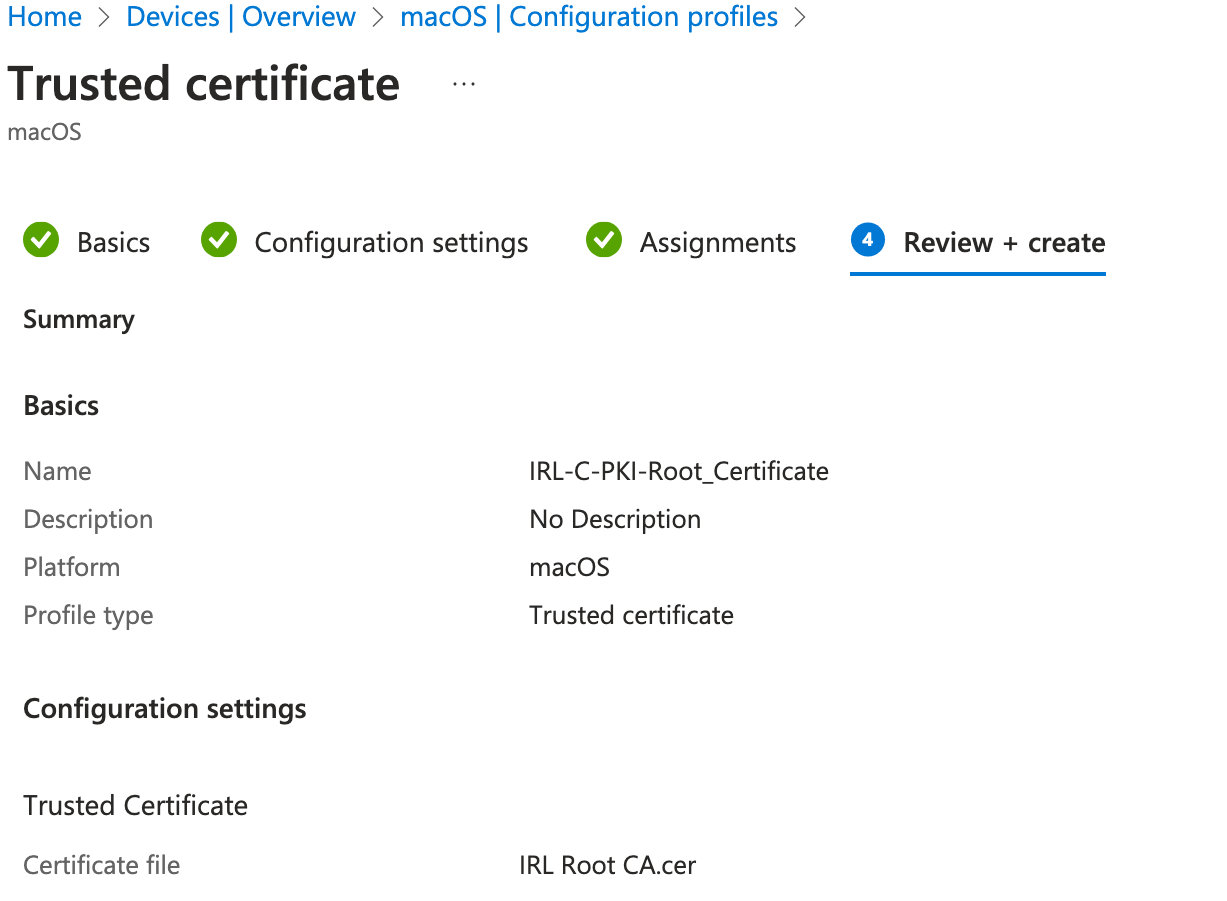
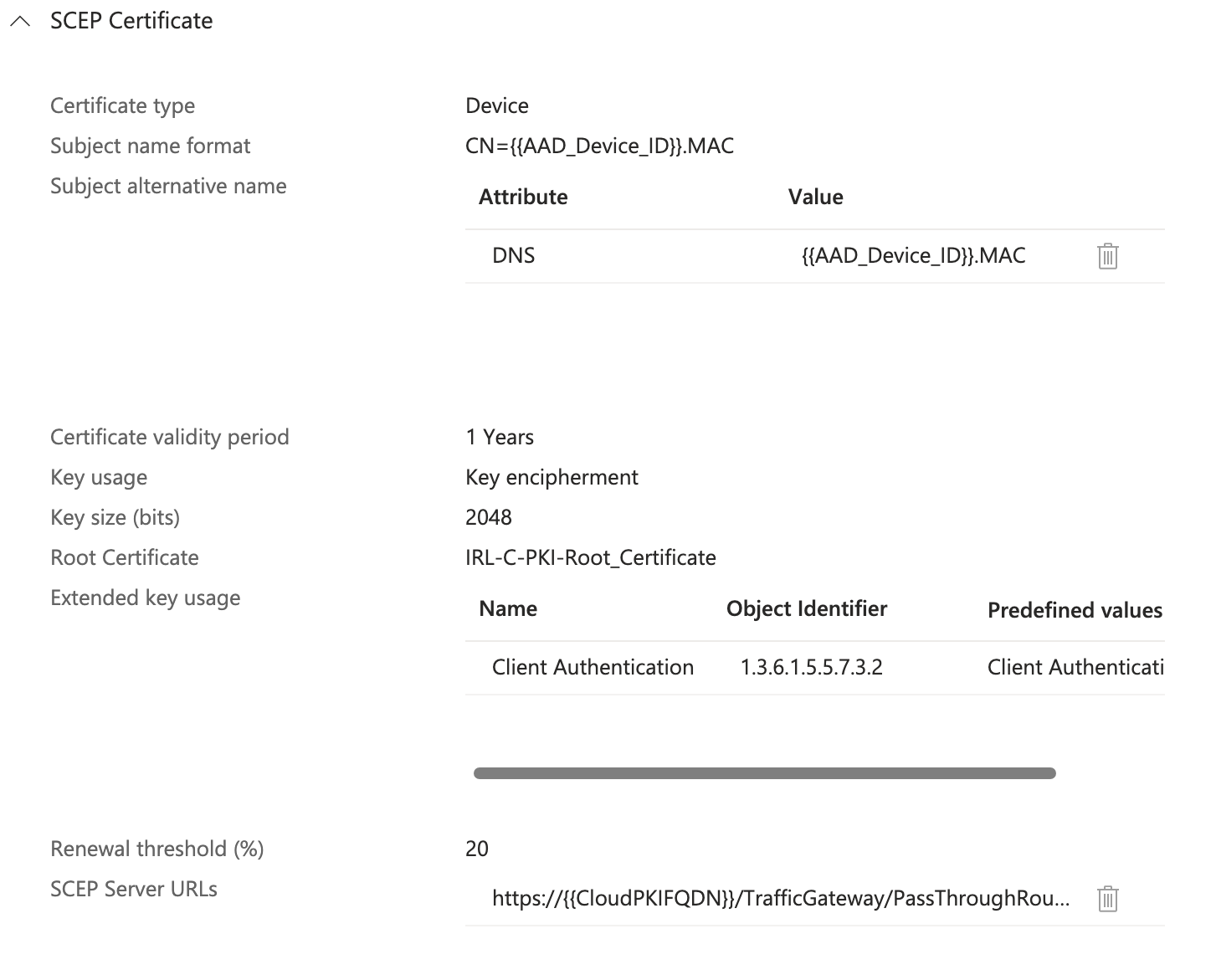
For every OS platform you intend to target, create a SCEP certificate profile, just as you did for the trusted certificate profiles. To obtain a leaf client authentication certificate from the issuing CA, using the SCEP certificate profile. This kind of certificate is utilized in scenarios involving certificate-based authentication, such as VPN and Wi-Fi access.
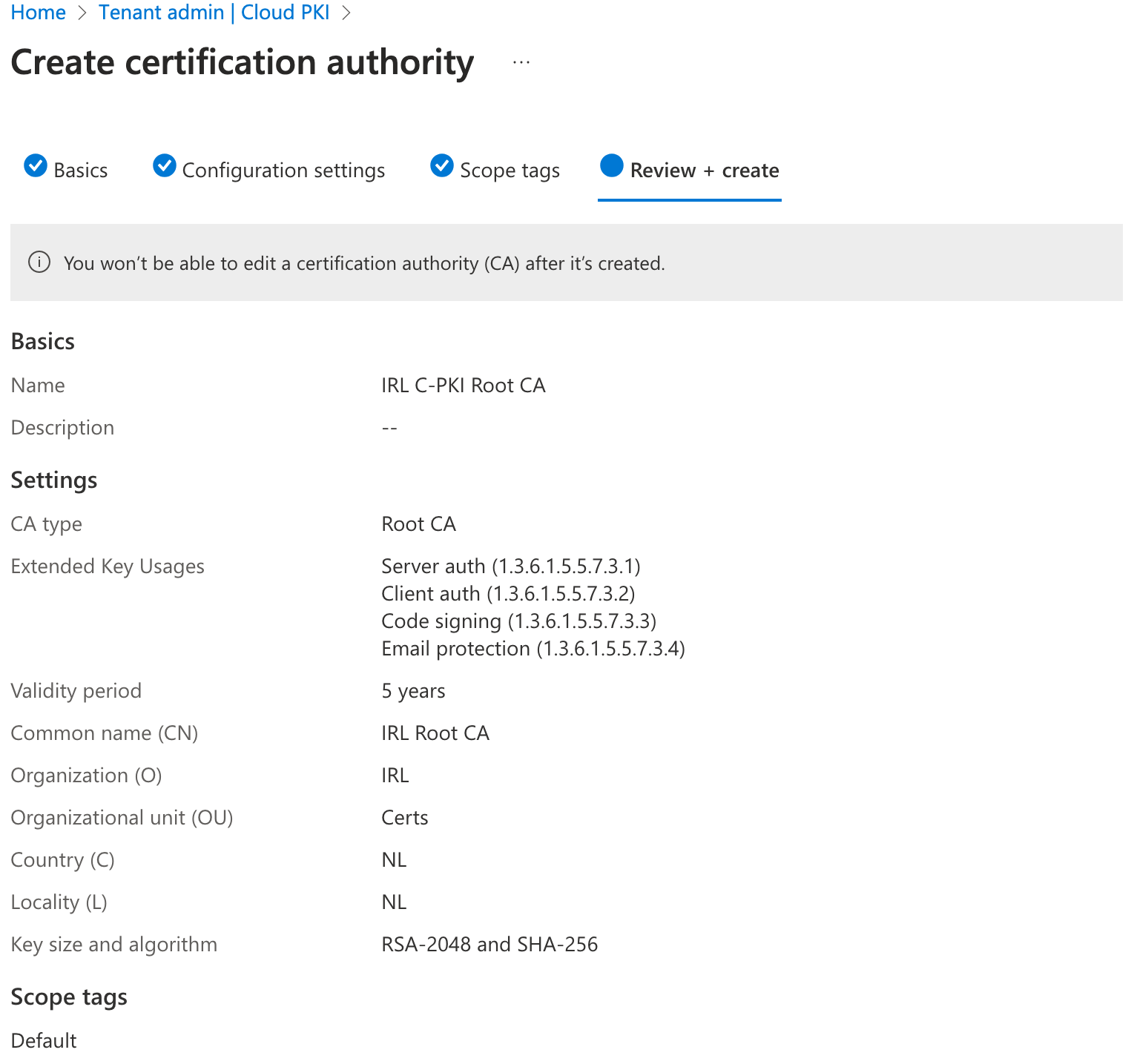
With Graph API, you may set up your Cloud PKI Root CA. Using the configurations I've previously specified, the Graph API request below will deploy a Root CA. I am using Postman to create the certificate. Make sure you adjust the necessary elements in accordance with your needs:
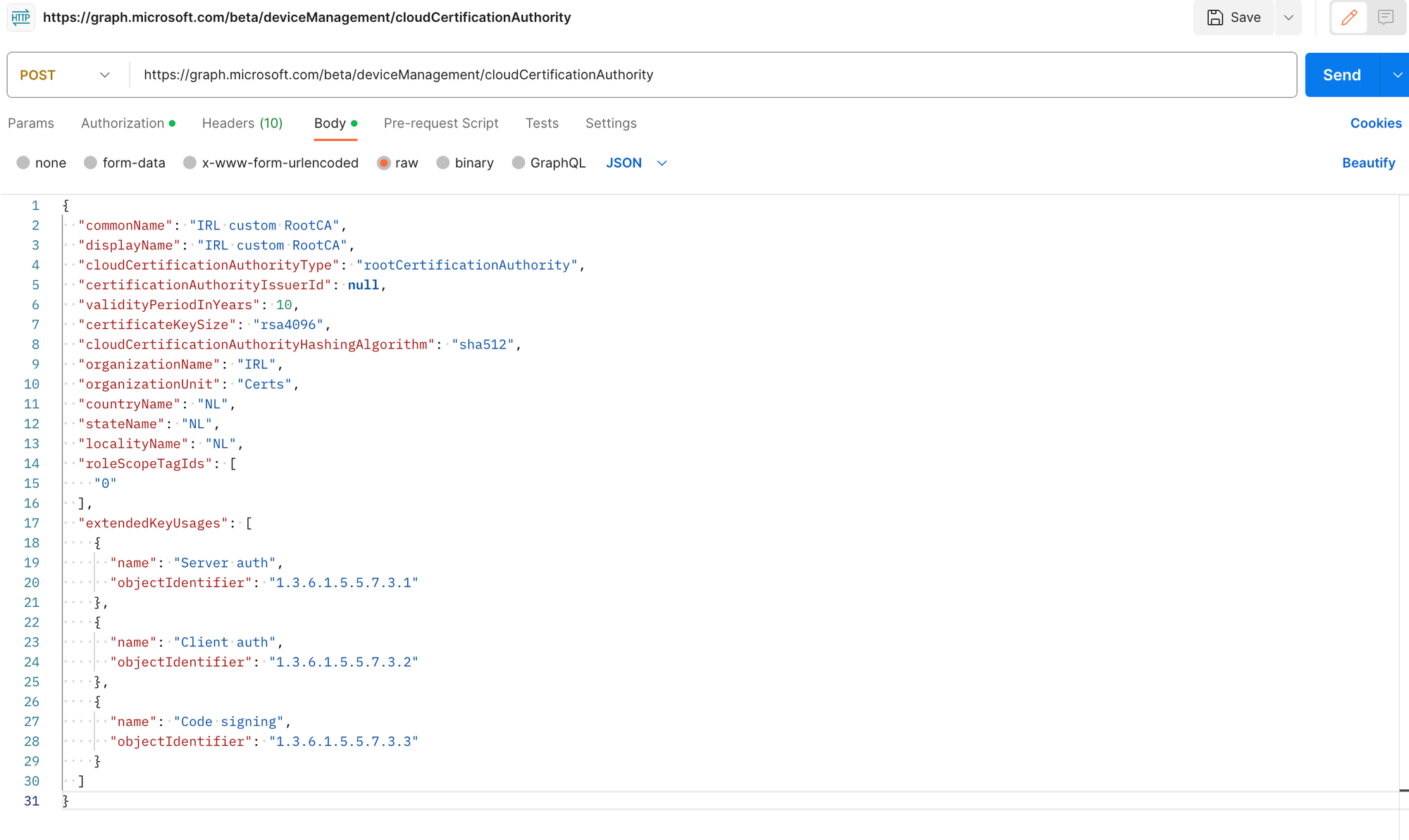
You will get a status code of 200 which means it has been created successfully.
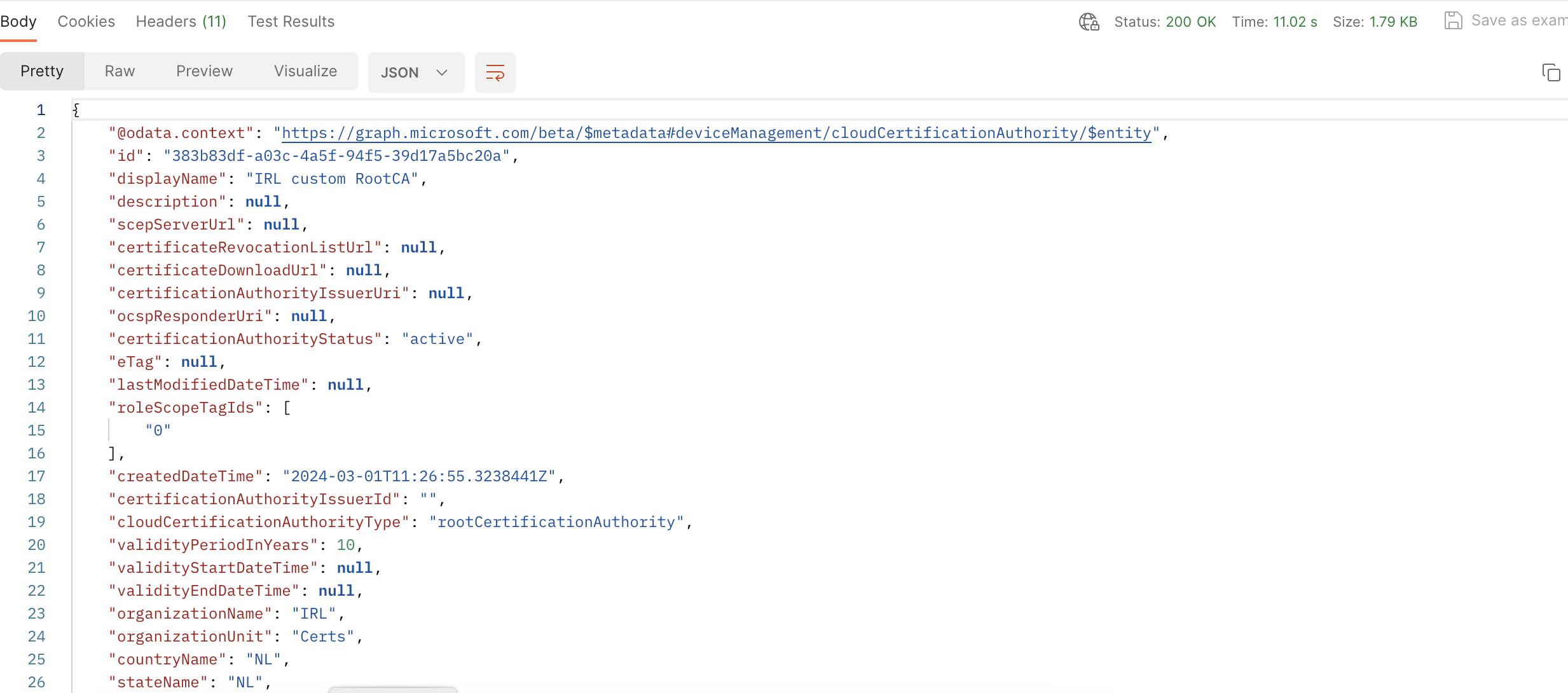
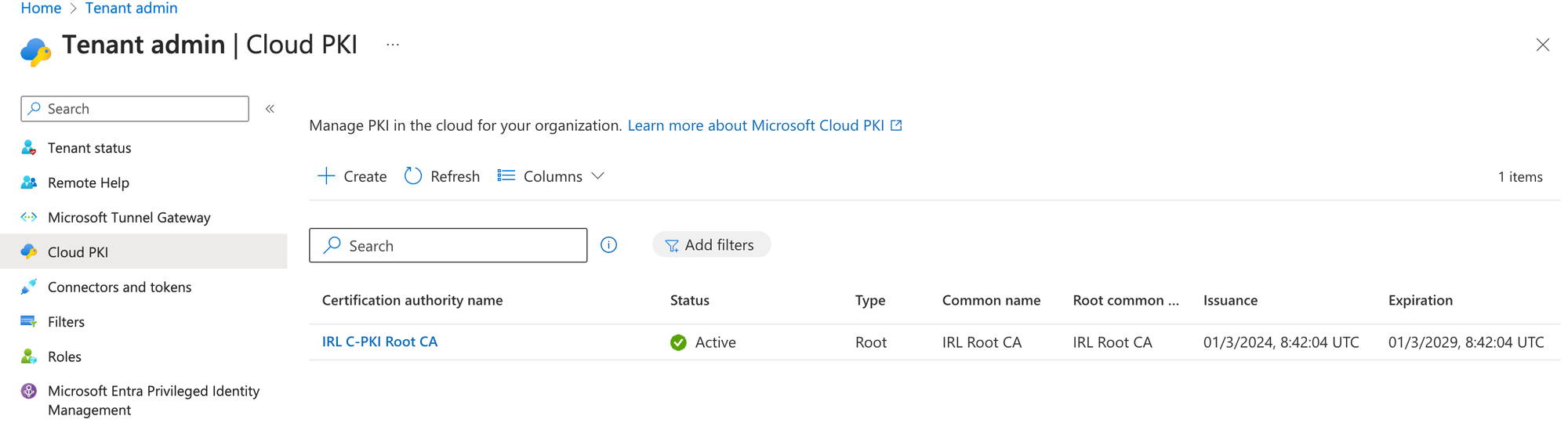
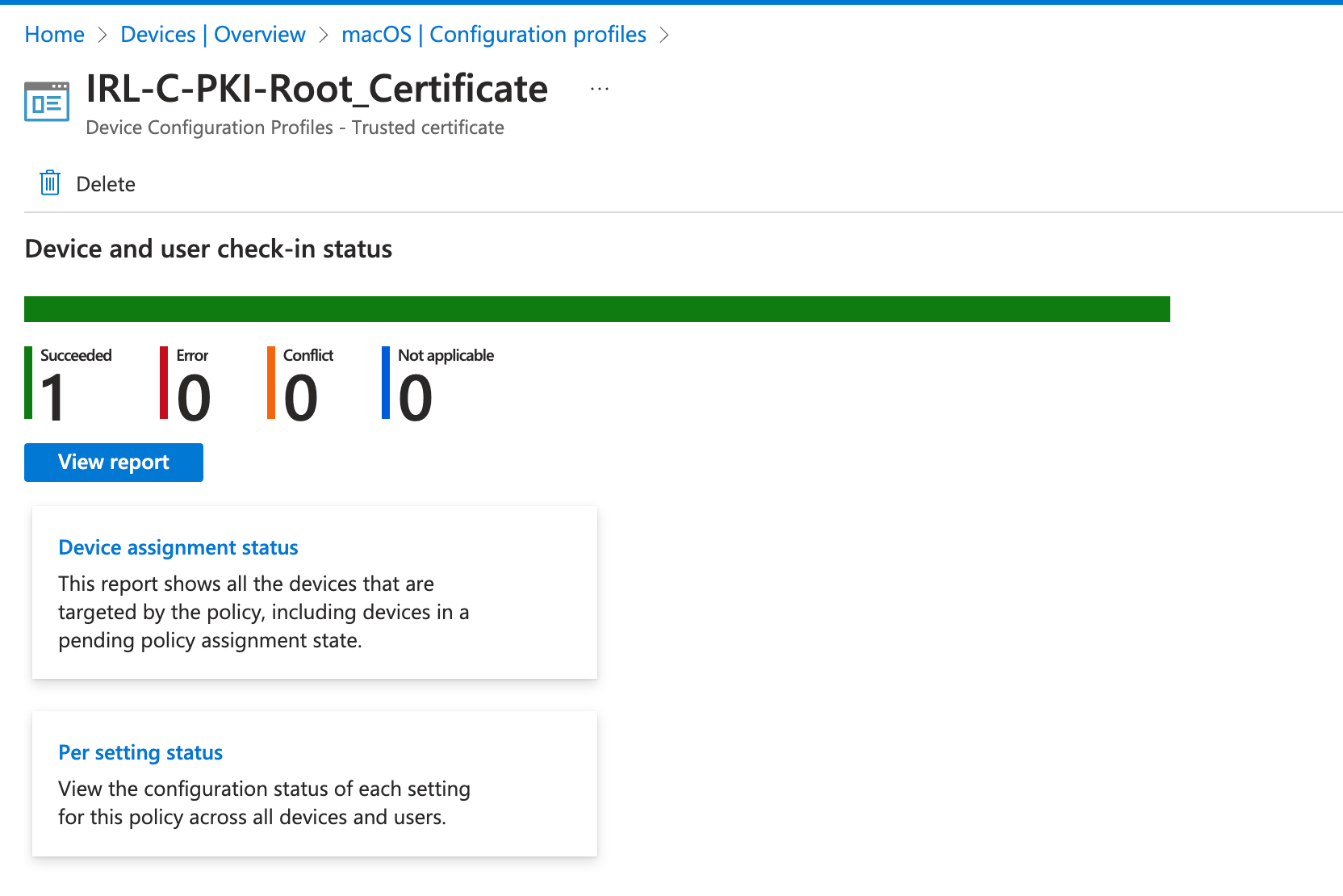
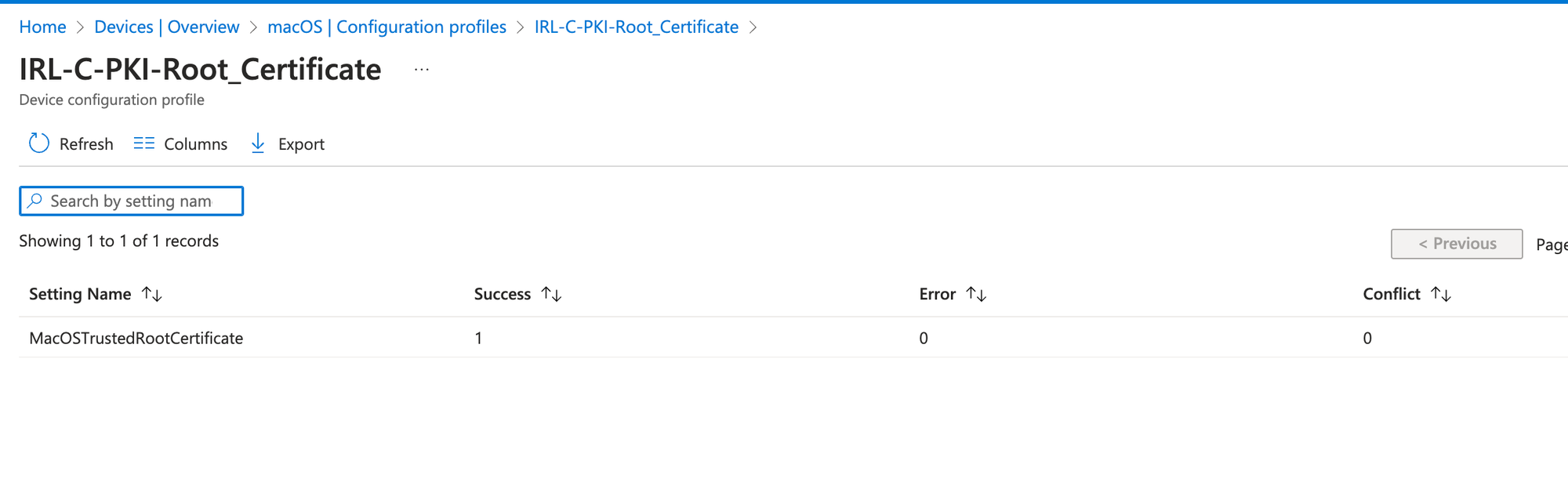
Let's verify this in Intune Admin Center:
Now, let's create the issuing certificate also using Postman.
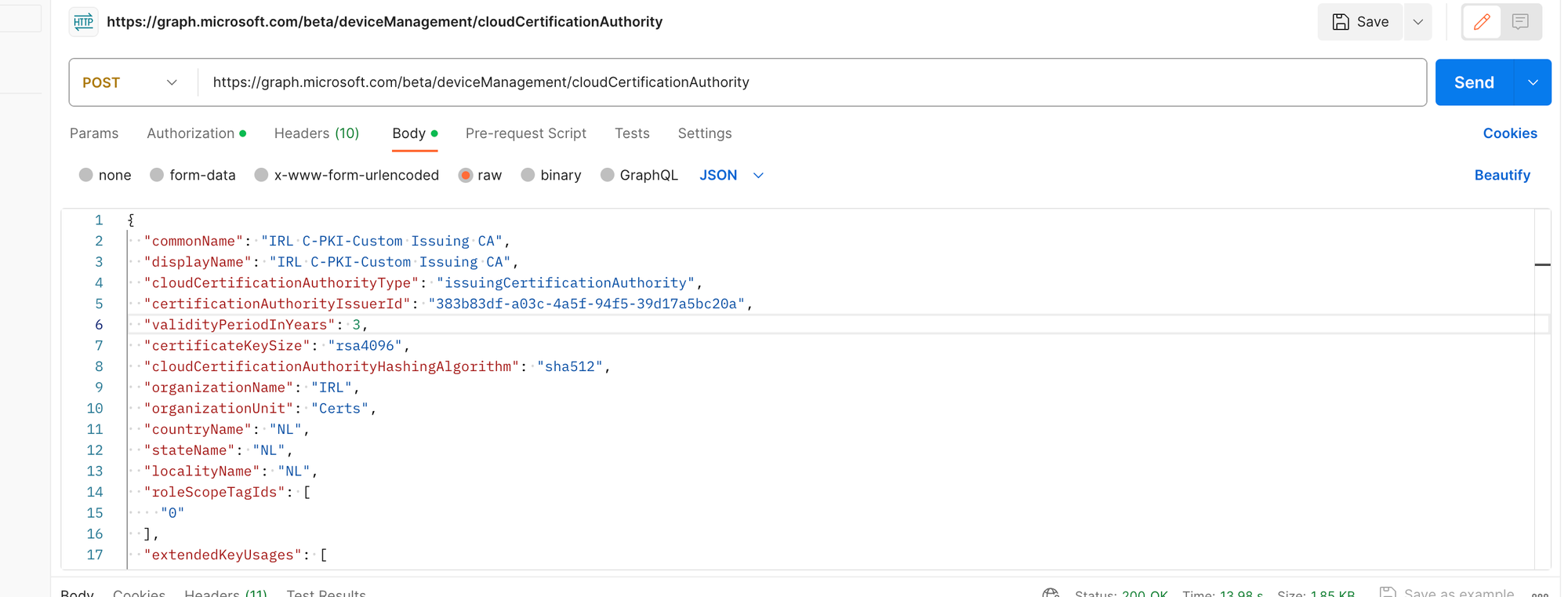
Status 200 - Successfully created.
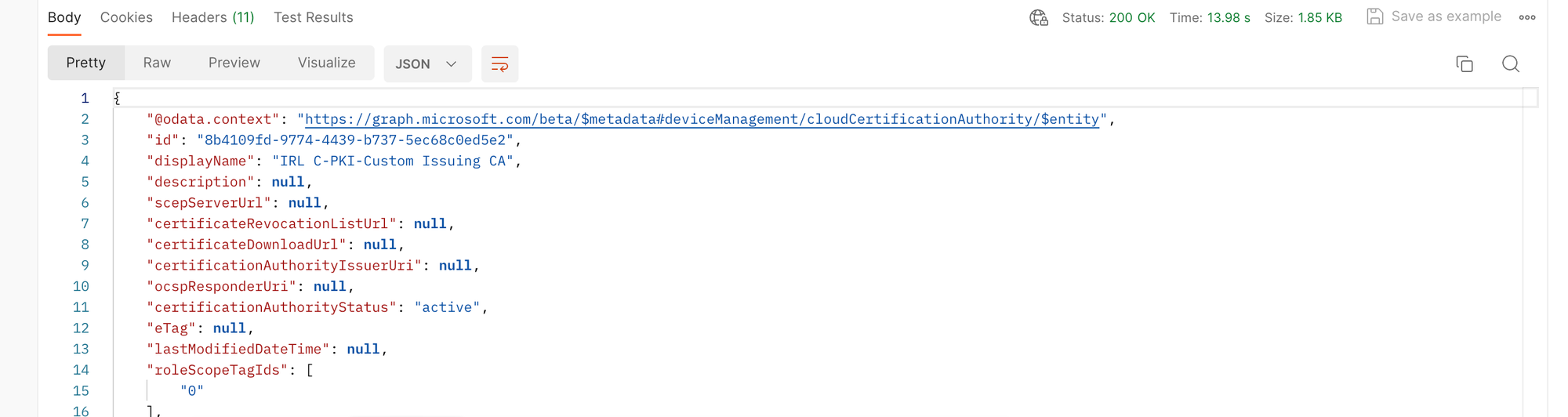
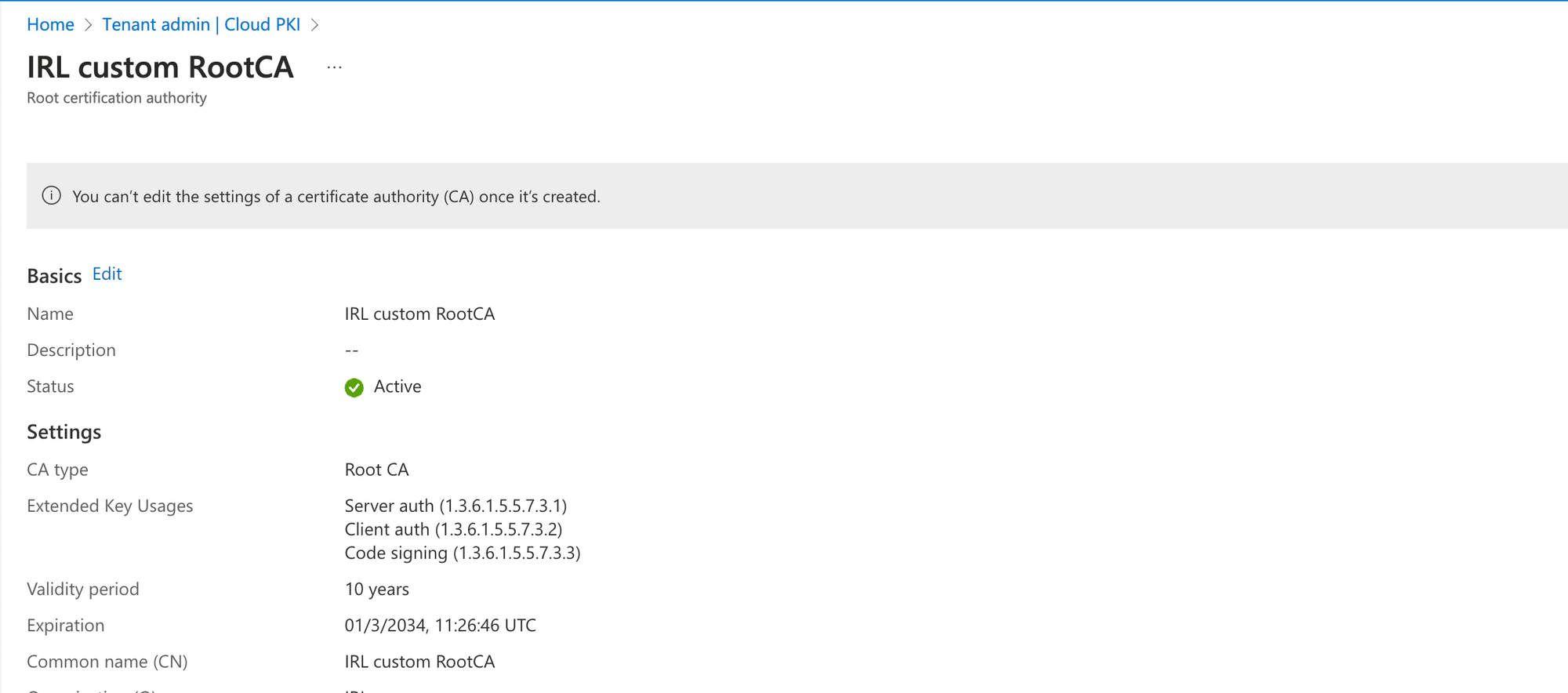
Verify in Intune Admin Center:
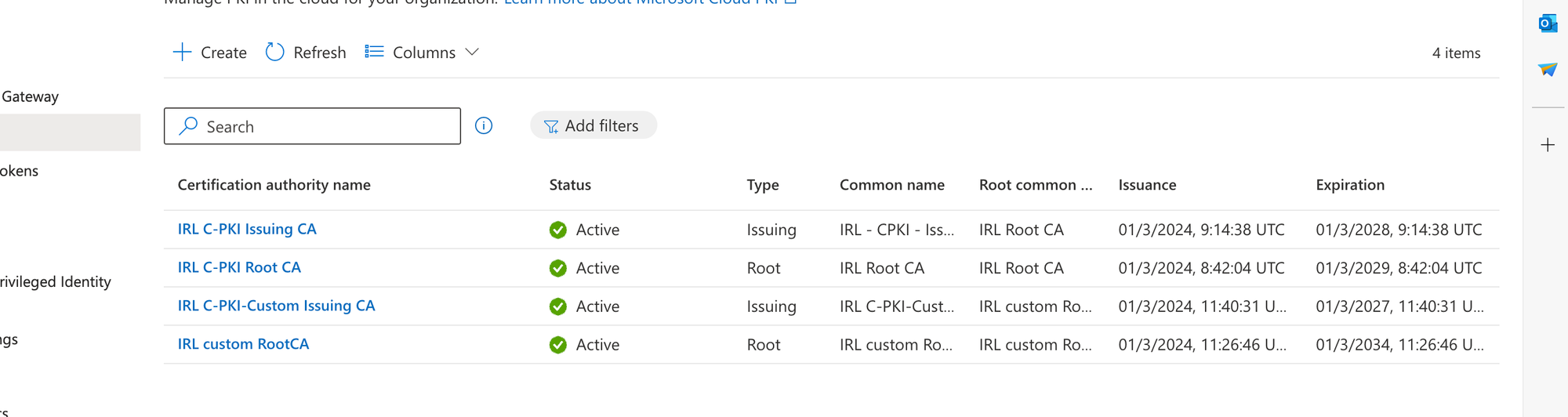
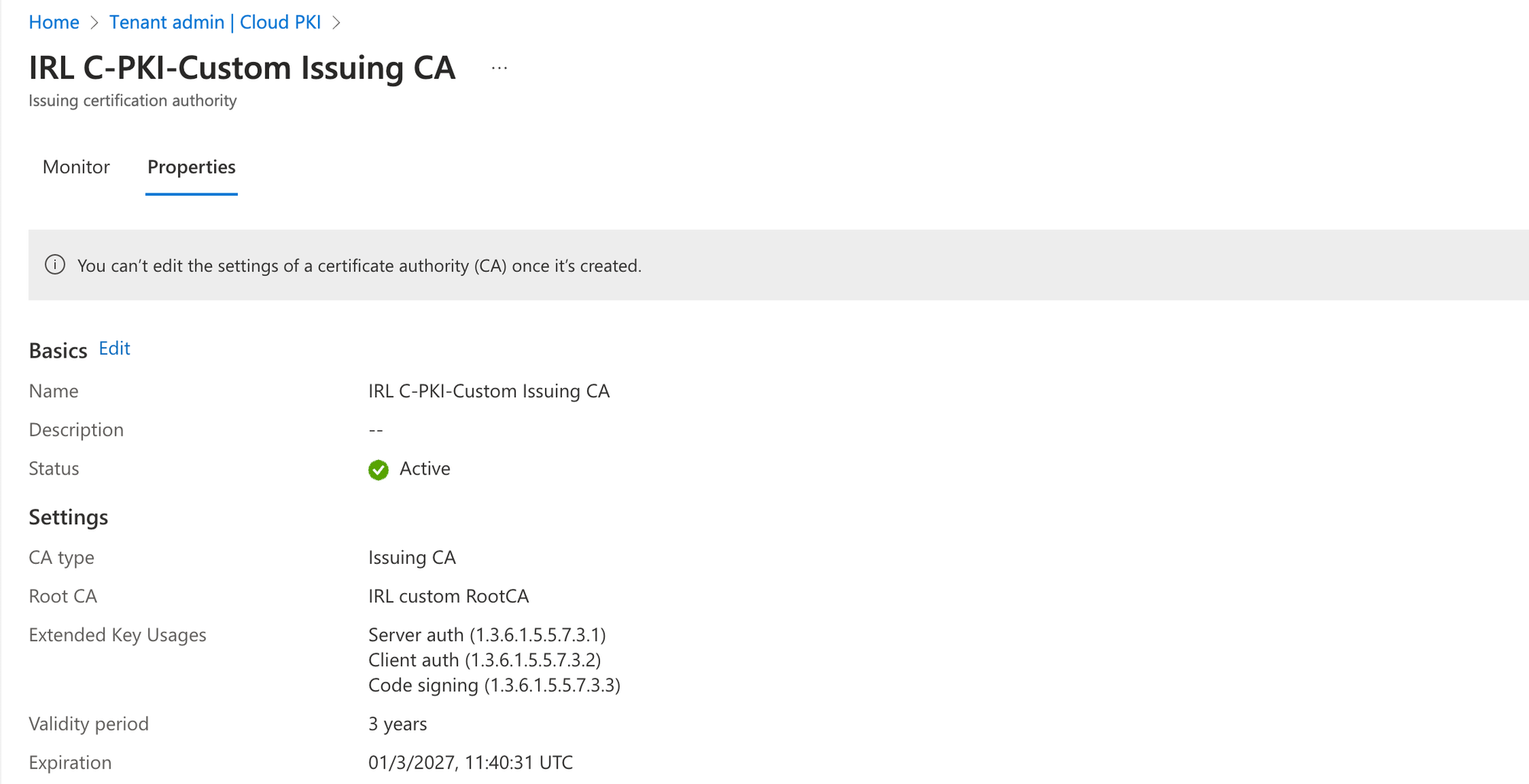
After configuring the CA, verify its integration with Intune by issuing a test certificate. Let's verify locally on a device to see the certificates installed:
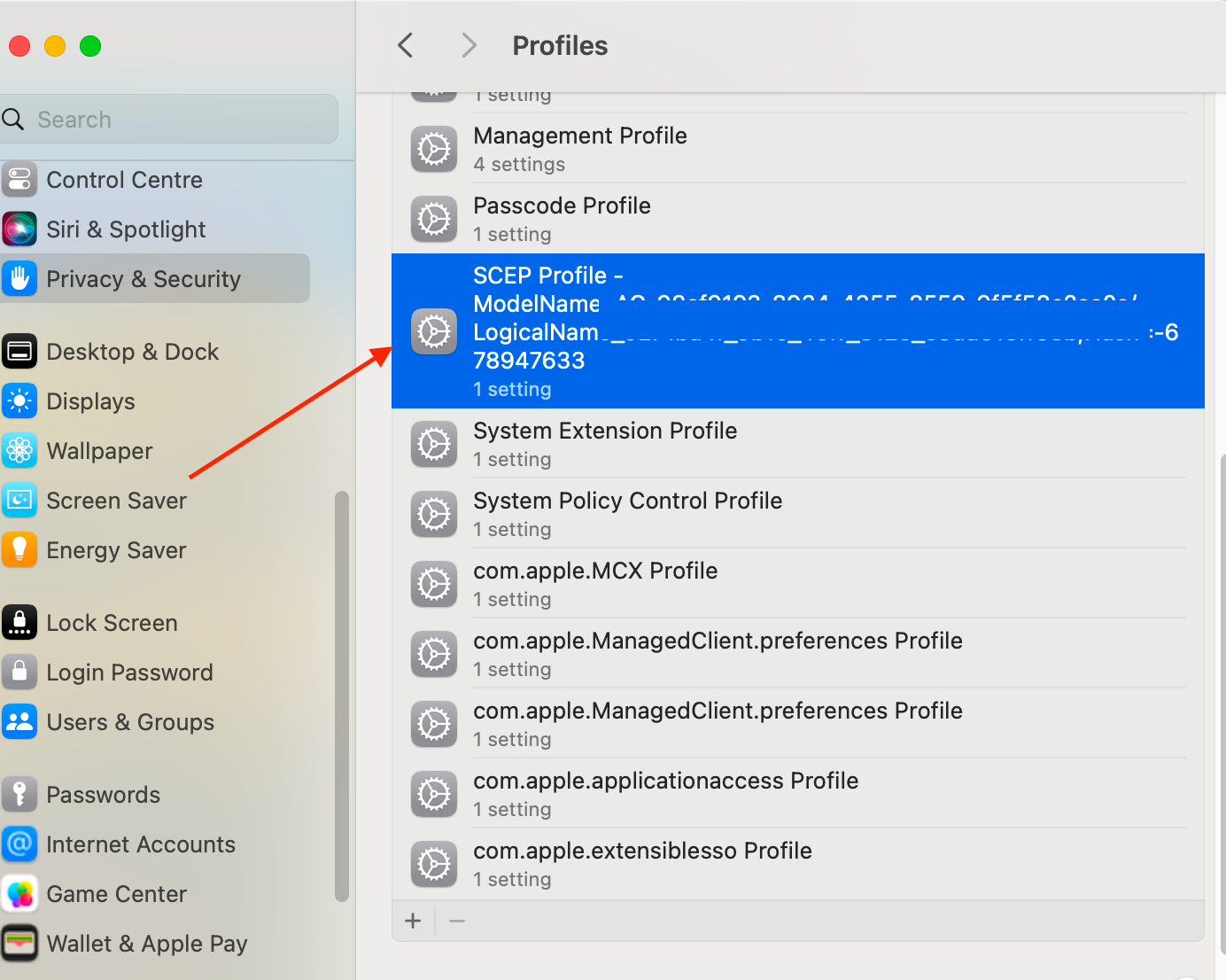
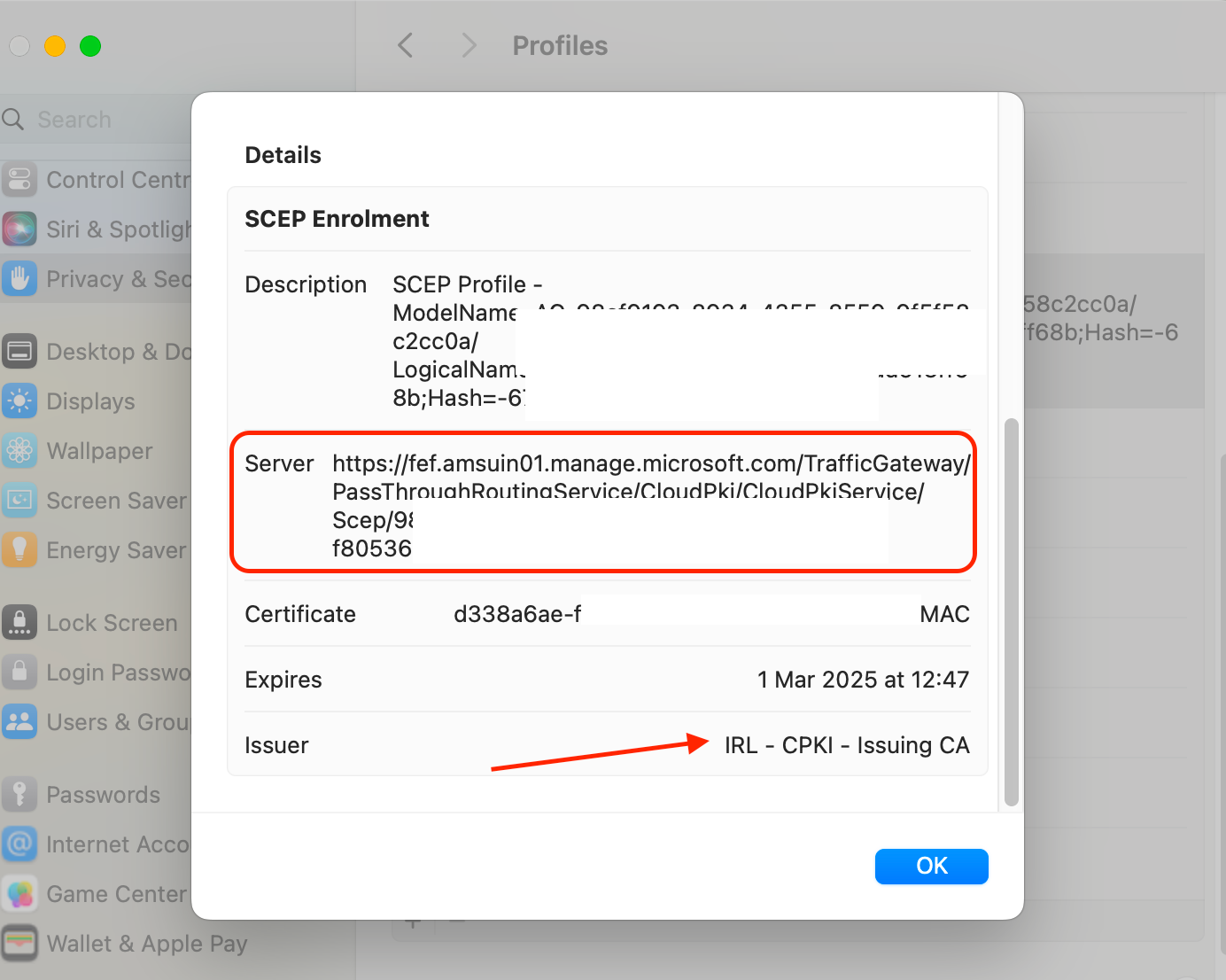
Deploying Cloud PKI in Microsoft Intune is a critical step towards securing your organization's digital communications and data while at the same time reducing your on-prem foot prints.. By carefully planning your deployment, configuring your CA, creating detailed certificate profiles, and closely monitoring the deployment process, you can ensure a successful integration. Remember, a well-implemented Cloud PKI infrastructure simplifies certificate management while bolstering security across your managed devices.